From asec.ahnlab.com
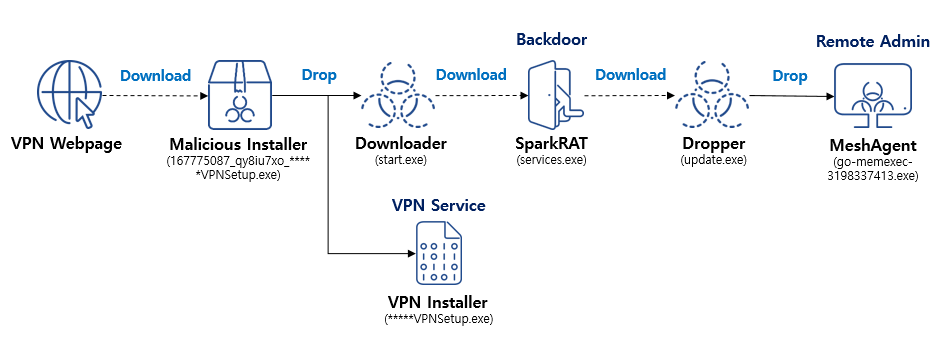
In the past, AhnLab Security Emergency response Center (ASEC) had shared the “SparkRAT Being Distributed Within a Korean VPN Installer” [1] case post and the “Analysis of Attack Cases: From Korean VPN Installations to MeshAgent Infections” [2] case post which covered the SparkRAT malware being distributed through a Korean VPN service provider’s installer.
ASEC has recently identified similar malware strains being distributed while being disguised as setup files for Korean VPN service providers and marketing program producers. Unlike the past cases where SparkRAT was used, Sliver C2 was used in the recent attacks [3] and techniques to evade detection were employed.
As of now, most websites of the affected companies provide normal setup files available for download. It is therefore uncertain whether the malware strain has been distributed as installers in official websites before being rectified like in past cases, or if there are other distribution paths. However, an investigation of the malware strains involved revealed that they were all related to the software provided by the same program development company. Most malware samples had certificates disguised as valid ones from this company. There were also multiple samples signed with valid certificates.
Malicious installers are still uploaded on the software download website provided by this company, so users may be unaware of this fact and install the file in question. In light of these facts, it seems that the threat actor attacked the development company and distributed installers with malware strains. Such types of attacks are steadily being launched from the first half of 2023.