From proofpoint.com
Key Takeaways
- Proofpoint identified a new malware we call WikiLoader.
- It has been observed delivered in multiple campaigns conducted by threat actors targeting Italian organizations.
- The malware uses multiple mechanisms to evade detection.
- It is named WikiLoader due to the malware making a request to Wikipedia and checking that the response has the string “The Free” in the contents.
- It is likely the use of this malware is available for sale to multiple cybercriminal groups.
Overview
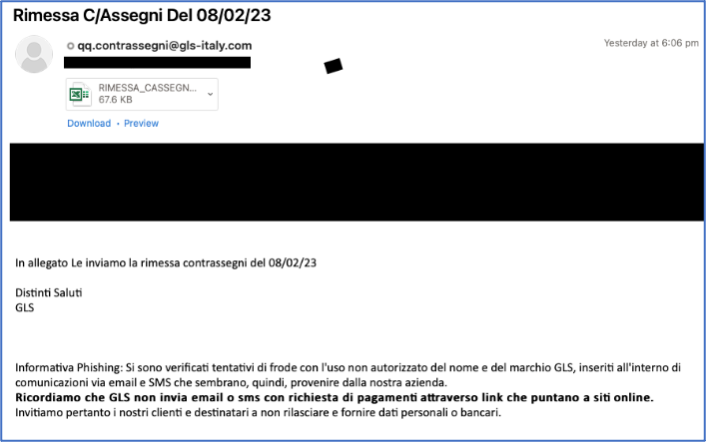
Proofpoint researchers identified a new malware we call WikiLoader. It was first identified in December 2022 being delivered by TA544, an actor that typically uses Ursnif malware to target Italian organizations. Proofpoint observed multiple subsequent campaigns, the majority of which targeted Italian organizations.
WikiLoader is a sophisticated downloader with the objective of installing a second malware payload. The malware contains interesting evasion techniques and custom implementation of code designed to make detection and analysis challenging. WikiLoader was likely developed as a malware that can be rented out to select cybercriminal threat actors.
Based on the observed use by multiple threat actors, Proofpoint anticipates this malware will likely be used by other threat actors, especially those operating as initial access brokers (IABs).