Cyber Security during the COVID-19 crisis
While the global healthcare community is faced with unprecedented challenges surrounding the coronavirus pandemic, citizens and organisations are fighting their own battles in cyberspace to thwart opportunism, the proliferation of associated cybercriminal activities, showing that this pandemic is nothing short of a hybrid threat.
Digital transformation during the "Great Lockdown"
It is fairly obvious that the pandemic is acting as an accelerator for digital transformation. The adoption of ICT for e-government services, working, entertainment and socialising has shown a growth rate comparable to the assorted coronavirus curves. The long discussions, debates, reflections, plans and strategy proposals for the digital transition of the society had to be abruptly cut and whatever plans were blissfully floating in drawers and "todo" trays are now materialising, together with newly introduced mandates in order to cope with the uniqueness of the present situation.
From a cybersecurity view, there are numerous fears and concerns. The cybersecurity research community is watchfully following the developments and responds by raising alerts, concerns and recommendations.
A representative example is the so-called contact tracing app. Although the lockdown seems to have curtailed the short-term impact of the virus, a significant challenge that remains to be addressed is the lockdown exit strategy in order to reboot the economy. As the nations took different and varying approaches for the lockdown, there are - as expected - different paradigms on the exit strategy. A common denominator across all strategies is the use of a software that will be installed on all smart phones that will allow the tracing and tracking of the citizens. The aim of this app is to keep a register of an individual's contact history in order to inform them if they have been in close proximity with an infected person. At the time of writing, countries across the globe are conducting pilots and trials. In the UK, there are trials undergoing in the Isle of Wight. The UK has adopted a different approach on the requirements and architecture of the app than in the rest of Europe. The research and academic community in the UK have raised concerns in this joint statement. UK's National Cyber Security Centre have published the details on the security and privacy requirements on the contact tracing app. The main issue with the UK approach is the privacy impact due to the centralised architecture adopted, where user activity will be captured by a third party. A good analysis and reflection is hosted by The Register.
The human factor
You can't teach an old dog new tricks. If you are a cybercriminal, you don't really need to, you have all the tools to conduct your business. At the same time, the users - potential victims - once more have been caught in keeping with their old habits. If there are ventures that are perspicacious of the "needs" of their customer base, these would be cybercriminal organisations. See for example the surge of domain registrations with a COVID-19 related domain (dataset:Domaintools):
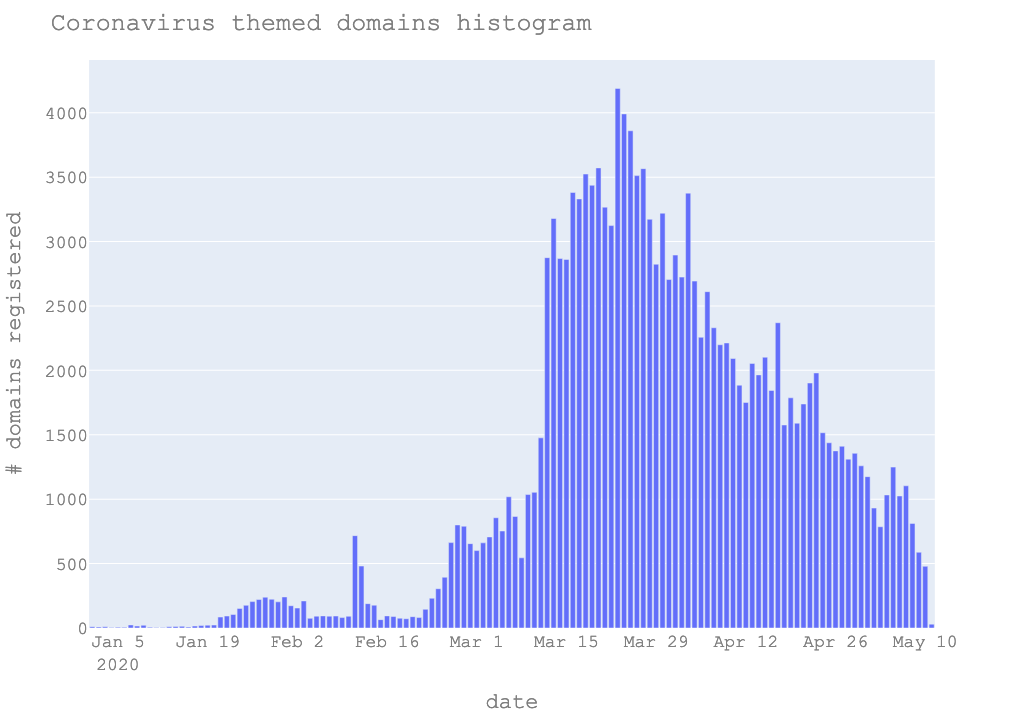
Although not all of the registered domains are necessarily linked with malicious campaigns and threat actors, the sheer volume of new domains is an indicator itself.
Human-in-the-loop
As on 5 April 2020, more than 120K coronavirus themed domains were registered. SANS have started a domain classifier project in an attempt to help the community single out the threat actors. If you wish to contribute visit this page.
Fear of missing out
Security was always about one's reactions to unfortunate situations and the coronavirus pandemic situation is no different; while we cannot control externalities, we are fully responsible for our responses and reactions. Not succumbing to fake ads, promises of miracle cures and online shops selling
assortments of protection artefacts is a great step to fighting the virus through social media immunity. An interesting analysis is presented in this short webcast:
NCSC's top tips for spotting telltale signs of phishing is emphasized:
- Authority - Is the sender claiming to be from someone official (like your bank, doctor, a solicitor, government department)? Criminals often pretend to be important people or organisations to trick you into doing what they want.
- Urgency - Are you told you have a limited time to respond (like in 24 hours or immediately)? Criminals often threaten you with fines or other negative consequences.
- Emotion - Does the message make you panic, fearful, hopeful or curious? Criminals often use threatening language, make false claims of support, or tease you into wanting to find out more.
- Scarcity - Is the message offering something in short supply (like concert tickets, money or a cure for medical conditions)? Fear of missing out on a good deal or opportunity can make you respond quickly.
- Current events - Are you expecting to see a message like this? Criminals often exploit current news stories, big events or specific times of year (like tax reporting) to make their scam seem more relevant to you.
Against the above and in order to support the users in managing the information overload, the remainder of this page contains links and analysis ordered from less to more technical.
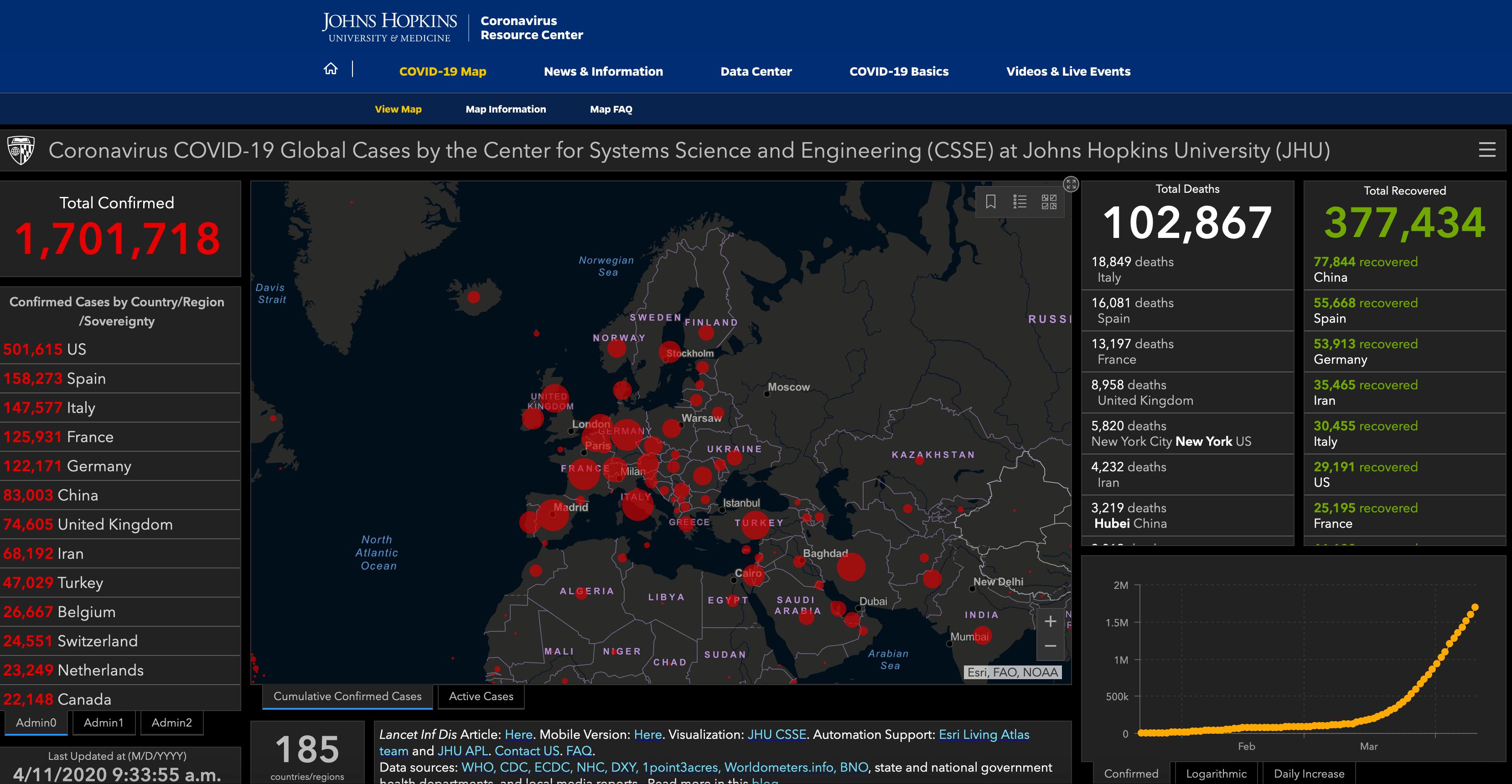
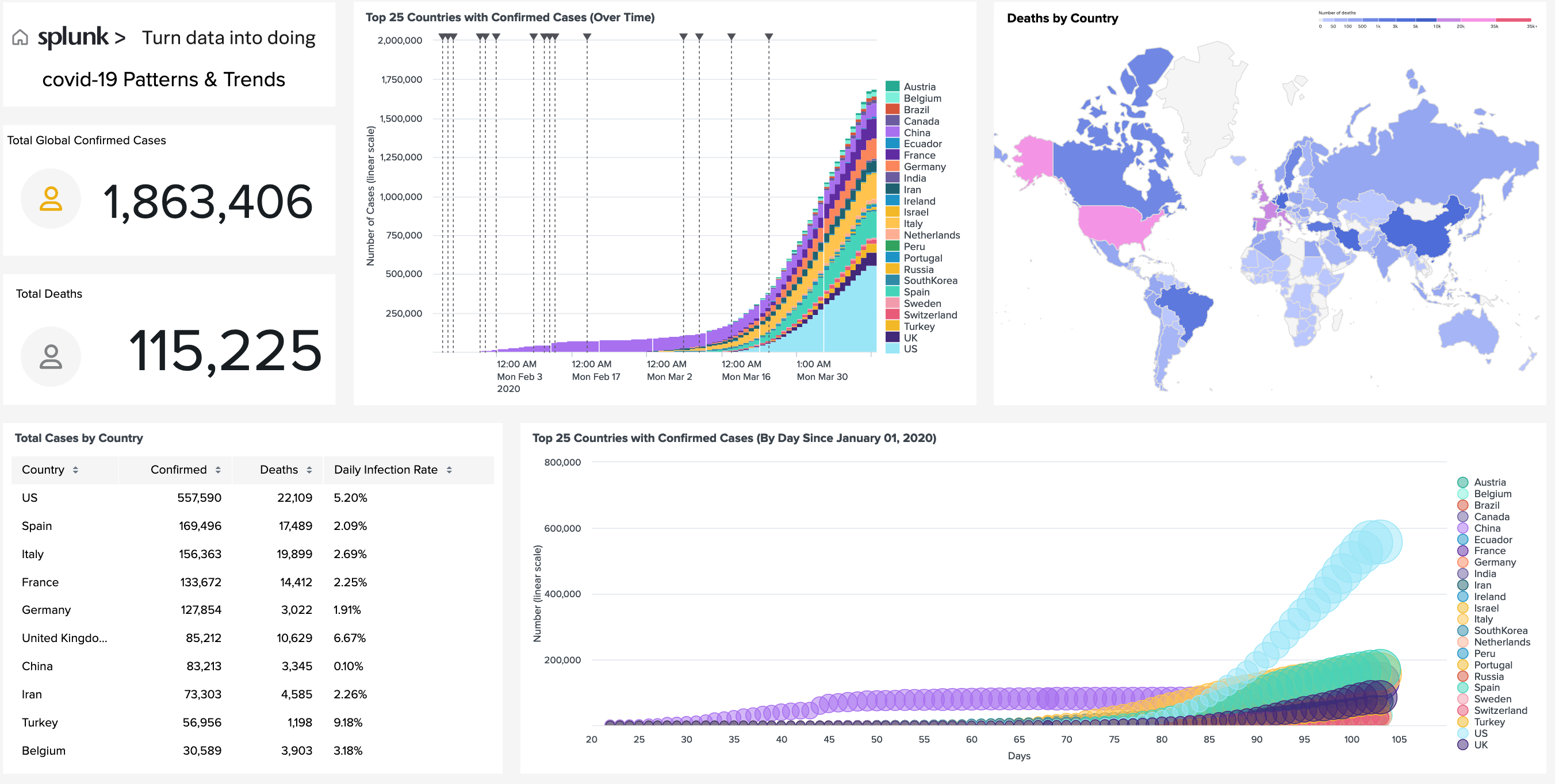
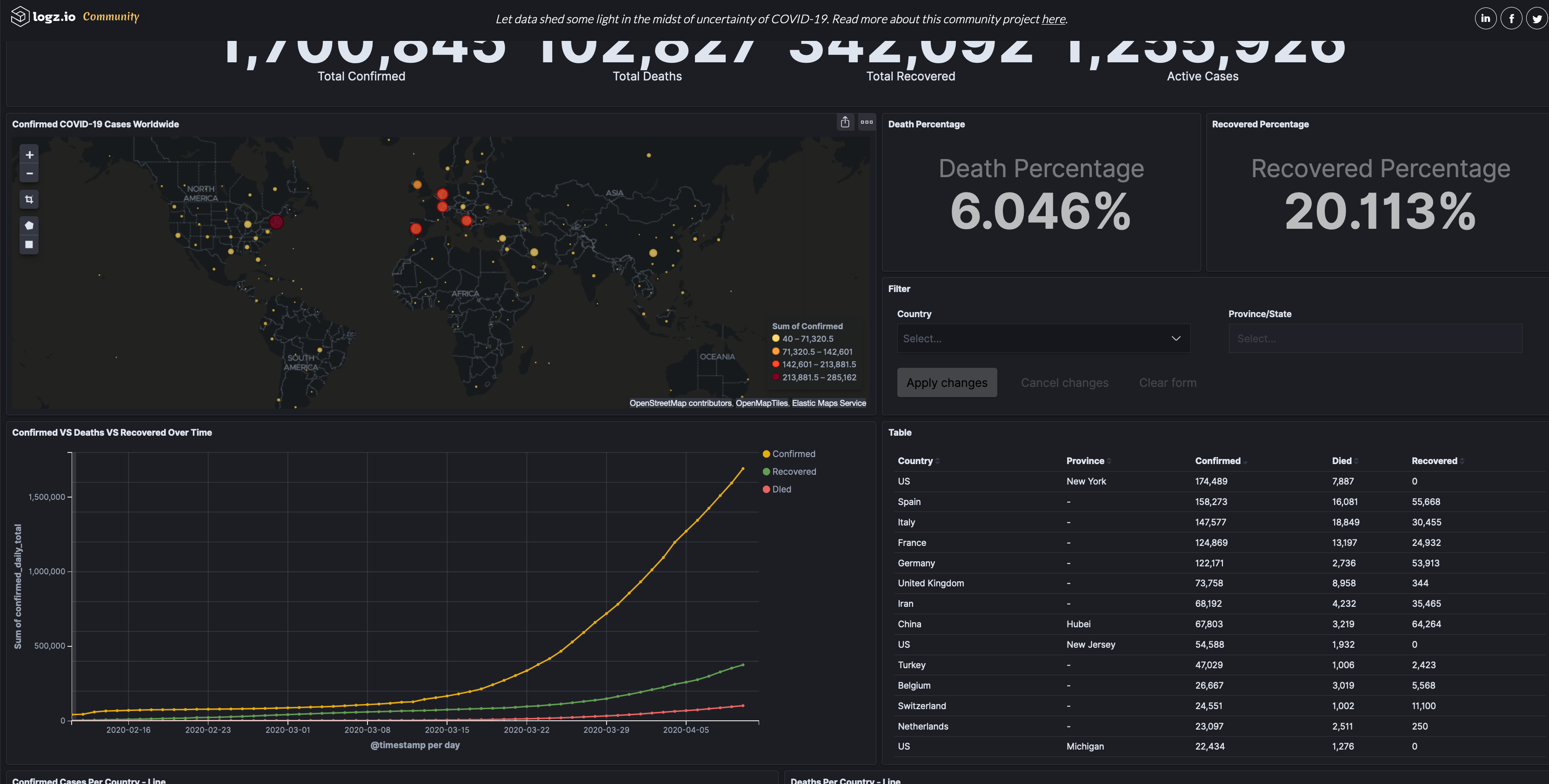
Coronavirus statistics and dashboards
Most of the dashboards seem to be constructed from data fed from wordlometers.info
As the data pertaining to the pandemic are constantly gathered, analysed and digested, there is a growing discontent and scepticism surrounding their quality. The bigger picture painted by the official data is becoming clearer and does not seem to convincingly represent reality as this is governed by intuition and nature's laws. The evident bias in the datasets resonates with the well-known concept in computer science of garbage in, garbage out.
However, even with the flawed datasets, data science and particularly the topics of data visualisation and visual analytics are becoming accessible to a wider audience who are exposed to concepts such as exponential growth, and the popular term 'flattening the curve'. Helen Kennedy from the University of Sheffield lists and contrast the various approaches and appearances of covid19 related graphs in the media in this informative article.
Teleworking
Challenges in having to work from home hit both those who were familiar with teleworking as well as those who rushed to create online accounts and experience the steep learning curve of ICT enabled teleworking. Teleworking to most meant performing some rather than all of their tasks remotely - unless the task involved a narrow type of activity using a computer and perhaps a pair of earphones and a mic,
such as a call centre operator.
The cybersecurity community has published a number of good practices with good advice, see for example ENISA's Tips for cybersecurity and Europol's Make your home a cyber safe stronghold infographic.
Social distancing, device edition
Needless to say, activity relating to personal life and work needs to be separated even on device-level. Many home schooling activities have now moved to include online activities and communication with the teachers. In some cases common infrastructures and software solutions are used for both school and work activities, so it is easy to establish that accounts, persistent logins and single sign on approaches can lead to tangled up workflows. A typical example is Microsoft Teams; many schools now use this as well as other businesses. You do not wish your child to hand in their work to your employer, or worse, send accidentally your confidential work to a teacher!
It is therefore critical to isolate work, school and family. It is understandable that this is becoming increasingly difficult to achieve, not only mentally but also technically especially if a household has limited devices and the only option is to share the same computer. If it is not possible to have a dedicated computer for the child's school activities, as a minimum create another dedicated local account on the device. By doing this, you ensure that any access on collaboration environments will be compartmentalised.
Zooming in
Zoom.us has clearly been placed among the top business success stories amid the crisis. A user friendly (and therefore limited security-by-default approach) teleconference service, gained a market share in a very short timeframe. Naturally, this led to a number of security challenges both due to the maturity of the software, its setup and the large pool of users who adopted it without a fully attuned cybersecurity posture. Indicatively, a new term was coined - ZoomBoming - illustrating the dynamic, fast-paced and fluid nature of cybersecurity.
While zoom is feverishly attempting to address the plethora of security issues, users need to focus on performing at least two tasks:
- check continuously and perform software updates. If you are using Zoom on a Mac in particular, avoid using this in the first place until Zoom issues patches
- do not advertise zoom links in email signatures
- always set a password per session
- consider using the waiting room feature
- as soon as the conference starts and all participants join, the conference manager should lock the conference to prevent others from blasting in
Check the status of Zoom vulnerabilities on cvedetails.com.
Use the following censys query to check where the Zoom servers are located: https://censys.io/ipv4/map?q=%22zoom+is+ok%21%22+AND+%22zoom.us%22&
It was observed that in early April some of Zoom's servers were located in China; Zoom changed this setting mid April.
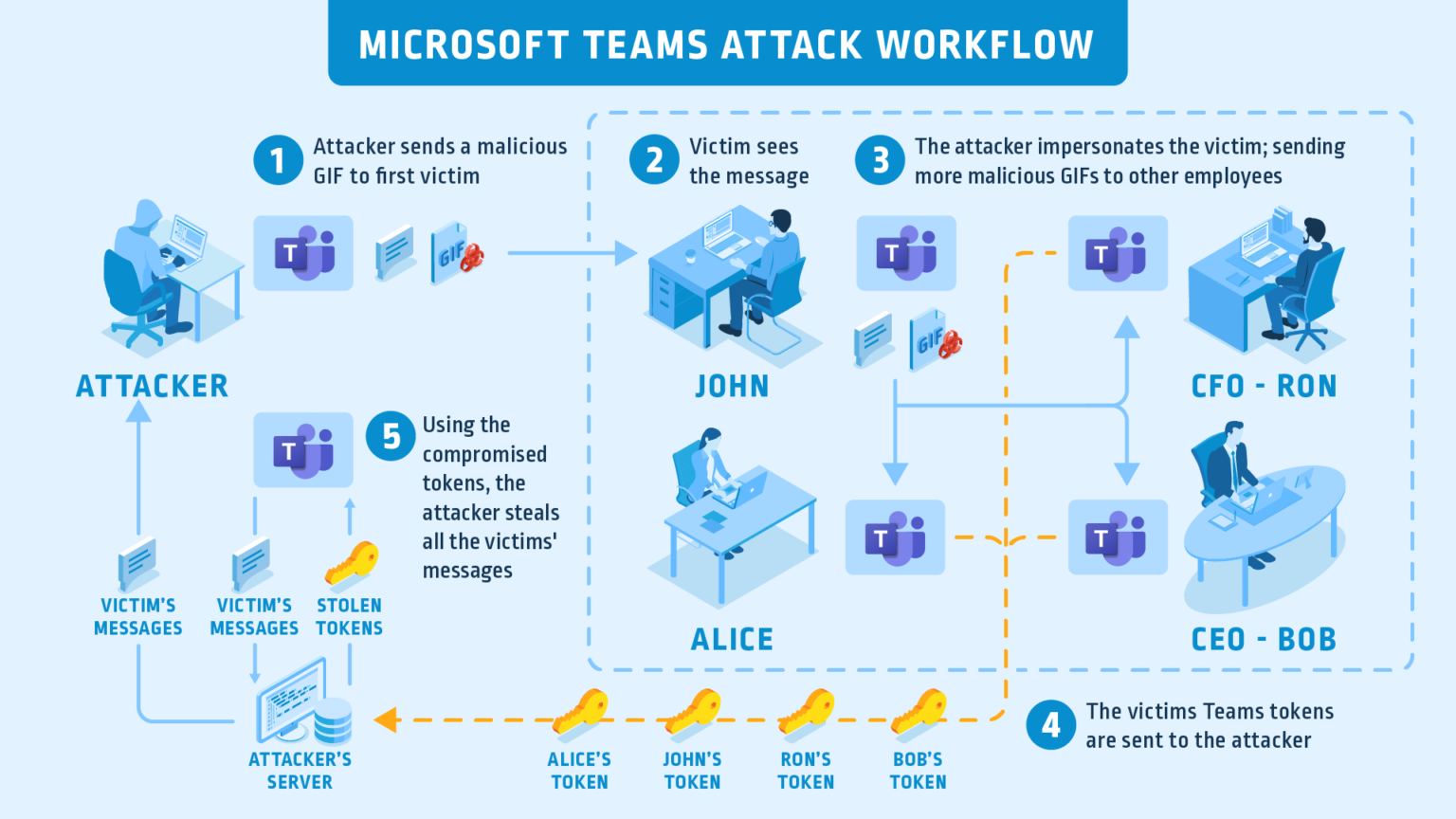
Microsoft Teams
However, although Zoom dominated the headlines as one of the most vulnerable conference software, vulnerabilities and attacks were lurking in other tools such as Teams.
Anyone using Teams prior to April 20, 2020 (and later, if they didn't update) were vulnerable to a critical vulnerability allowing the attack to spread in Teams in a worm-like manner, by just viewing a GIF image. The malicious GIF could scrape the user's data and perform an account take over:
Microsoft were highly responsive and issued a patch on 20.4.2020. For more information and technical details check Cyberark's post here.
Blocklists and Indicators of Compromise
Incident response depends on good quality cyber threat intelligence information. We have identified the following feeds, providers and sources that are performing the feat of sieving and producing the indicators:
Dedicated coronavirus lists
- CyberThreatCoalition - https://blocklist.cyberthreatcoalition.org/
- ThreatConnect - https://threatconnect.com/blog/cal-covid19-themed-newly-registered-domains-feed/
- NCSC & CISA
- DomainTools - https://www.domaintools.com/resources/blog/free-covid-19-threat-list-domain-risk-assessments-for-coronavirus-threats
- Parth D. Maniar's github list - https://github.com/parthdmaniar/coronavirus-covid-19-SARS-CoV-2-IoCs
- Sophos labs github list - https://github.com/sophoslabs/covid-iocs
Generic lists containing coronavirus
- URLHaus - https://urlhaus.abuse.ch/
- Openphish - https://openphish.com/feed.txt