From blog.sucuri.net
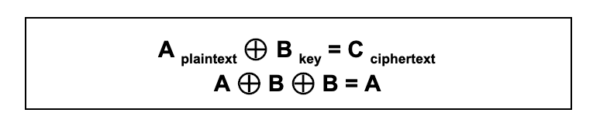
In the past, we’ve mentioned how the PHP XOR bitwise operator (represented by the caret ^) can be used to encrypt a malware’s source code. This operator makes it more difficult to determine if encrypted code is malicious, or if it is trying to protect a legitimate developer’s code. However, that’s not the only way that XOR can be used to hide malicious data. This is what we will explore today.