From thehackernews.com
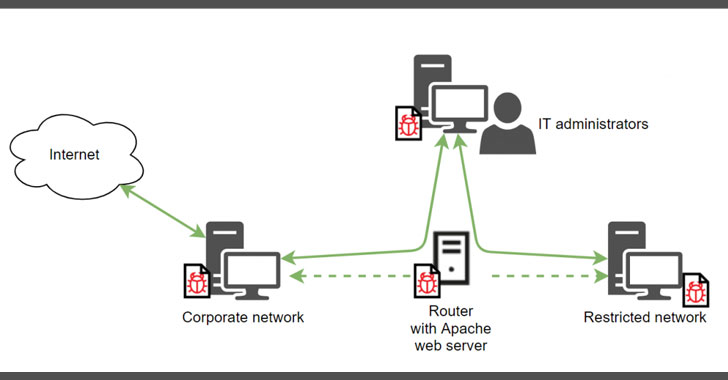
A prolific North Korean state-sponsored hacking group has been tied to a new ongoing espionage campaign aimed at exfiltrating sensitive information from organizations in the defense industry.
Attributing the attacks with high confidence to the Lazarus Group, the new findings from Kaspersky signal an expansion of the APT actor’s tactics by going beyond the usual gamut of financially-motivated crimes to fund the cash-strapped regime.
This broadening of its strategic interests happened in early 2020 by leveraging a tool called ThreatNeedle, researchers Vyacheslav Kopeytsev and Seongsu Park said in a Thursday write-up.