From securityonline.info
A PowerShell script to collect memory and (triage) disk forensics for incident response investigations.
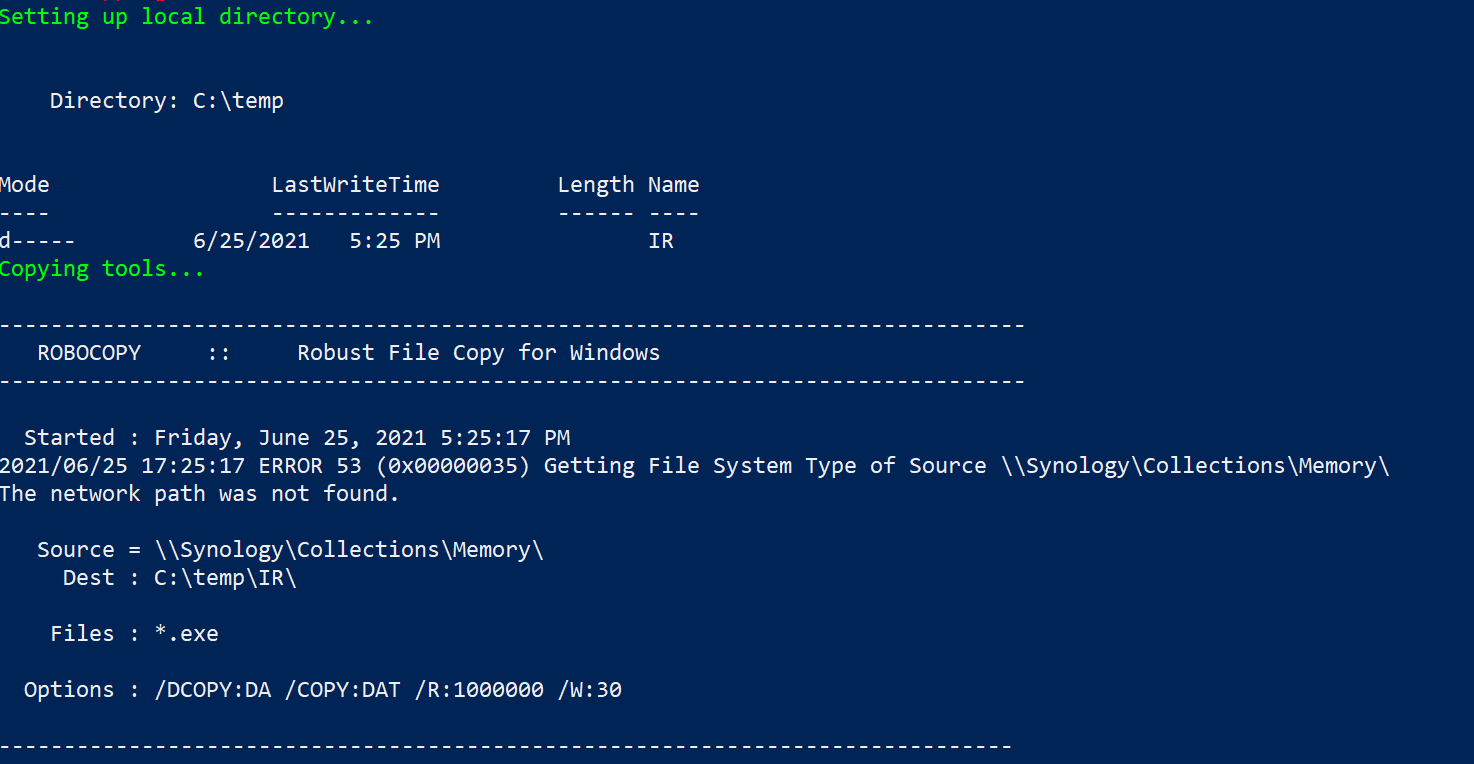
The script leverages a network share, from which it will access and copy the required executables and subsequently upload the acquired evidence to the same share post-collection.
Permission requirements for the said directory will be dependent on the nuances of the environment and what credentials are used for the script execution (interactive vs. automation)
In the demonstration code, a network location of \Synology\Collections can be seen. This should be changed to reflect the specifics of your environment.
Collections folder needs to include:
- subdirectory KAPE; copy the directory from the existing install
- subdirectory MEMORY; 7za.exe command line version of 7zip and winpmem.exe