From any.run
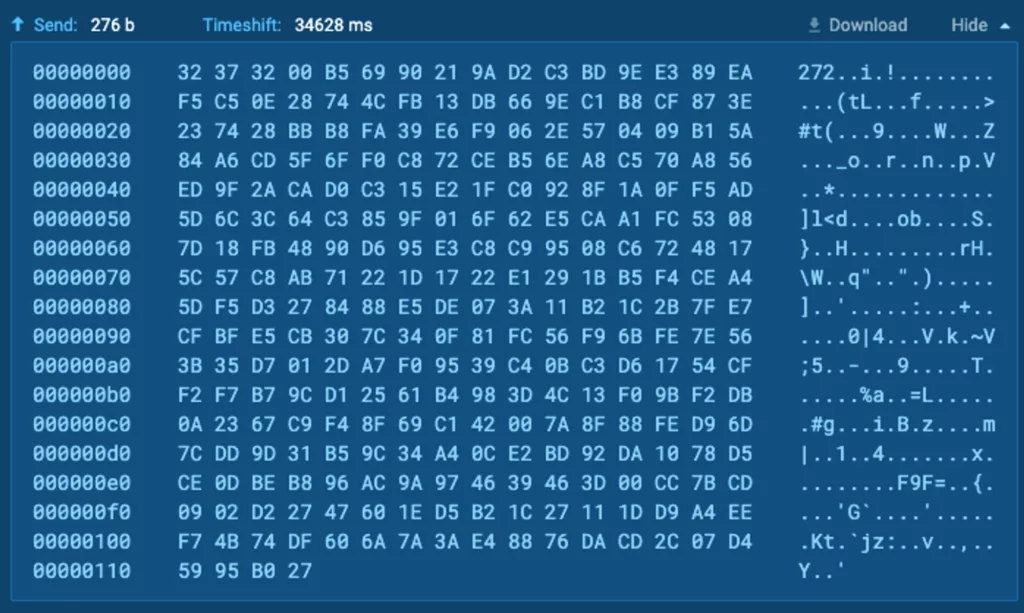
In this article, our guest author Igal Lytzki (0xToxin on Twitter) will explore and understand the dynamics occurring when a successful connection is established between the XWorm operating server and a user who has fallen victim to executing this malware.
Throughout this article, Igal will investigate the encryption of the communication between the client and the server, uncover the methods to decrypt it, and identify the potential data and commands the server can transmit to the client.