From malware.news
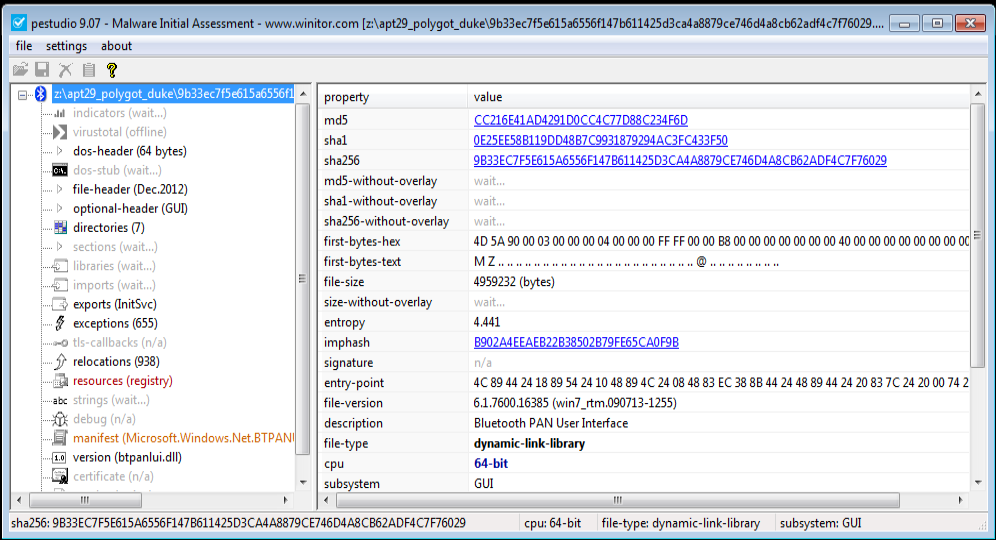
In this blog, i will be unpacking , static and dynamic analysis of trojan “PolyGlot Duke” from APT29. For this blog we only focus on Unpacking.
From malware.news

In this blog, i will be unpacking , static and dynamic analysis of trojan “PolyGlot Duke” from APT29. For this blog we only focus on Unpacking.