From securityonline.info
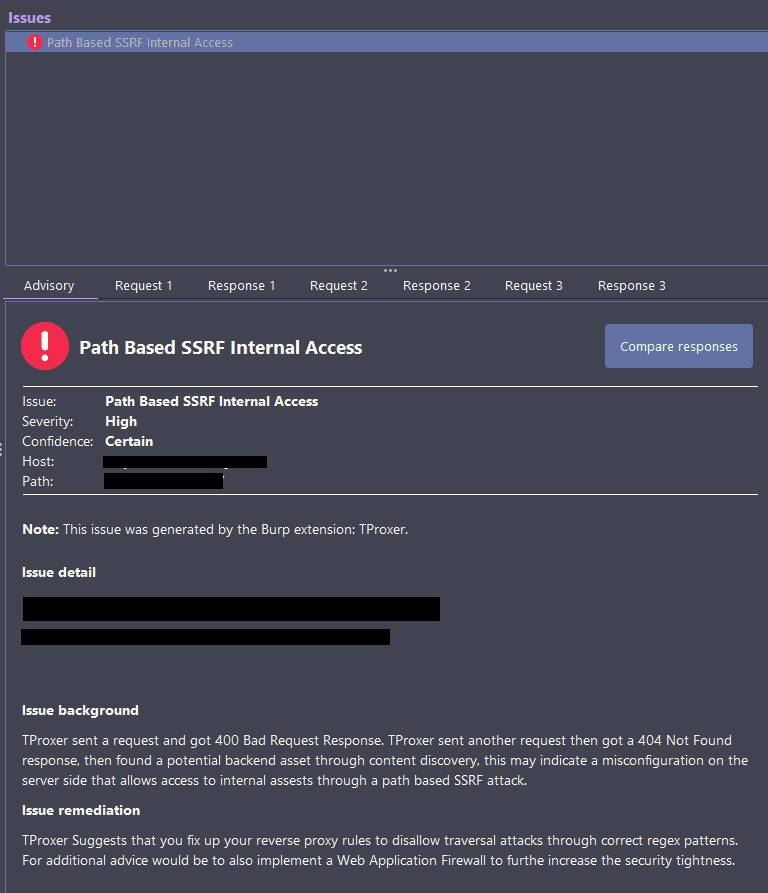
How it works
- Attempts to gain access to internal APIs or files through a path-based SSRF attack. For instance https://www.example.com/api/v1/users we try the payload /..;/..;/..;/..;/ hoping for a 400 Bad Request:
- Then the Algorithm tries to find the potential internal API root with: https://www.example.com/api/v1/users/..;/..;/..;/ hoping for a 404 Not Found
- Then, we try to discover content, if anything is found it performs an additional test to see if it’s 100% internal and worth investigating.
- Supports manual activation through a context menu.
- Payloads are supplied by the user under a dedicated tab, default values are stored under query payloads.txt
- You can also select your own wordlist
- Issues are added under the Issue Activity tab.