From malware.news
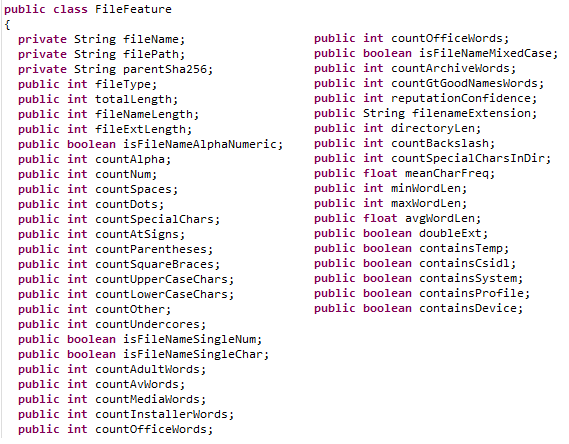
In the recent weeks I’ve been doing some research into Symantec EDR and looking into the technologies that are used to generate the incidents and events inside of the platform. In the hope to get a better understanding of the detection process and mechanisms within.
Seeing a file classified as malicious or an incident being declared is all good and well. But without providing context to the analyst or the one looking at these incidents it quickly becomes a game of blind trust and in my opinion if we’re writing detections or responding incidents we need all the context and information we can get.