From securityonline.info
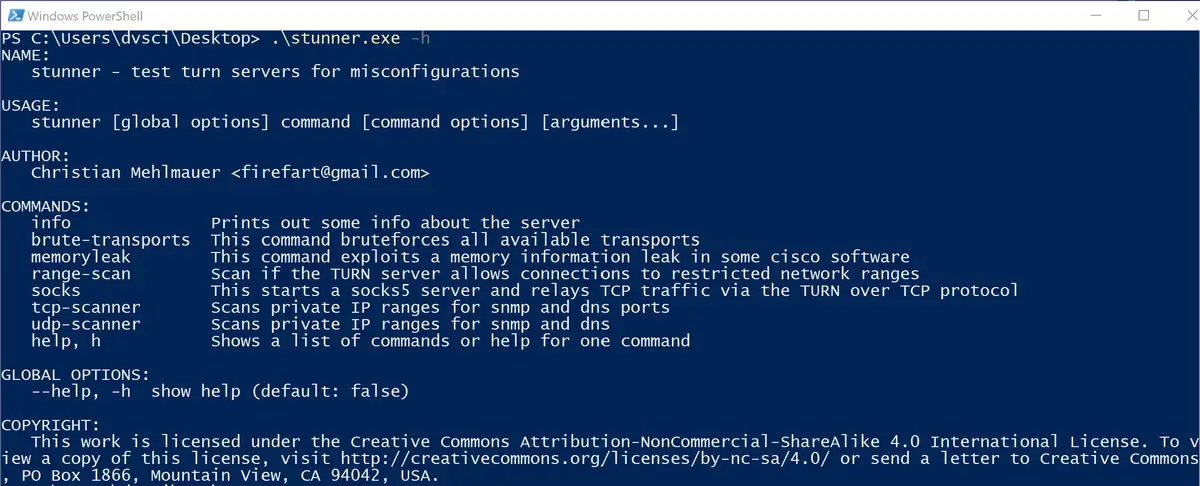
The first step is to get the required data. I suggest to launch Wireshark in the background and just join a meeting via Burp to collect all HTTP and Websocket traffic. Next search your burp history for some keywords related to TURN like 3478, password, credential, and username (be sure to also check the websocket tab for these keywords). This might reveal the turn server and the protocol (UDP and TCP endpoints might have different ports) and the credentials used to connect. If you can’t find the data in burp start looking at Wireshark to identify the traffic. If it’s on a non-standard port (anything else than 3478) decode the protocol in Wireshark via a right-click as STUN. This should show you the username used to connect and you can use this information to search burps history even further for the required data. Please note that Wireshark can’t show you the password as the password is used to hash some package contents so it can not be reversed.