From hakin9.org
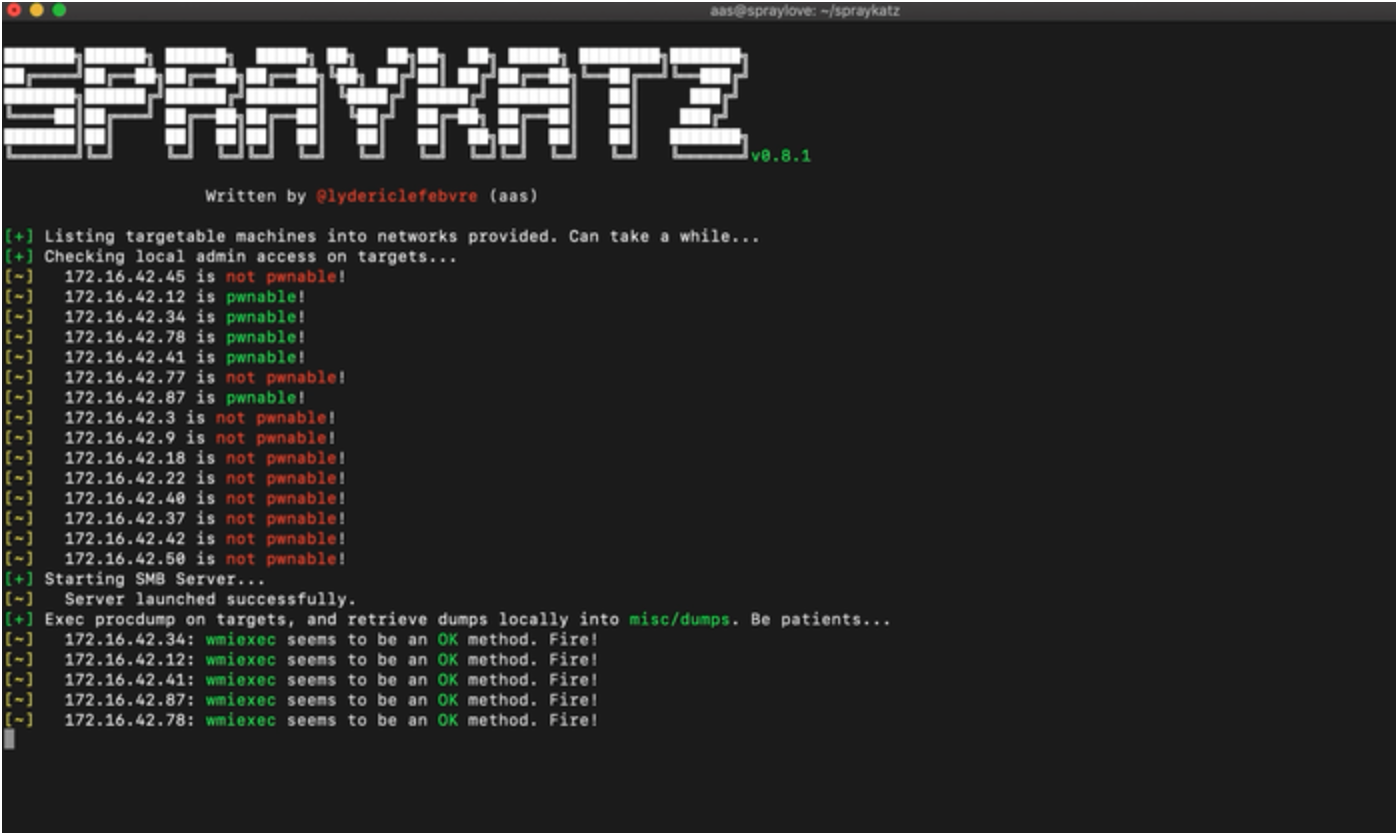
Spraykatz is a tool without any pretention able to retrieve credentials on Windows machines and large Active Directory environments.
It simply tries to procdump machines and parse dumps remotely in order to avoid detections by antivirus softwares as much as possible.