From securityonline.info
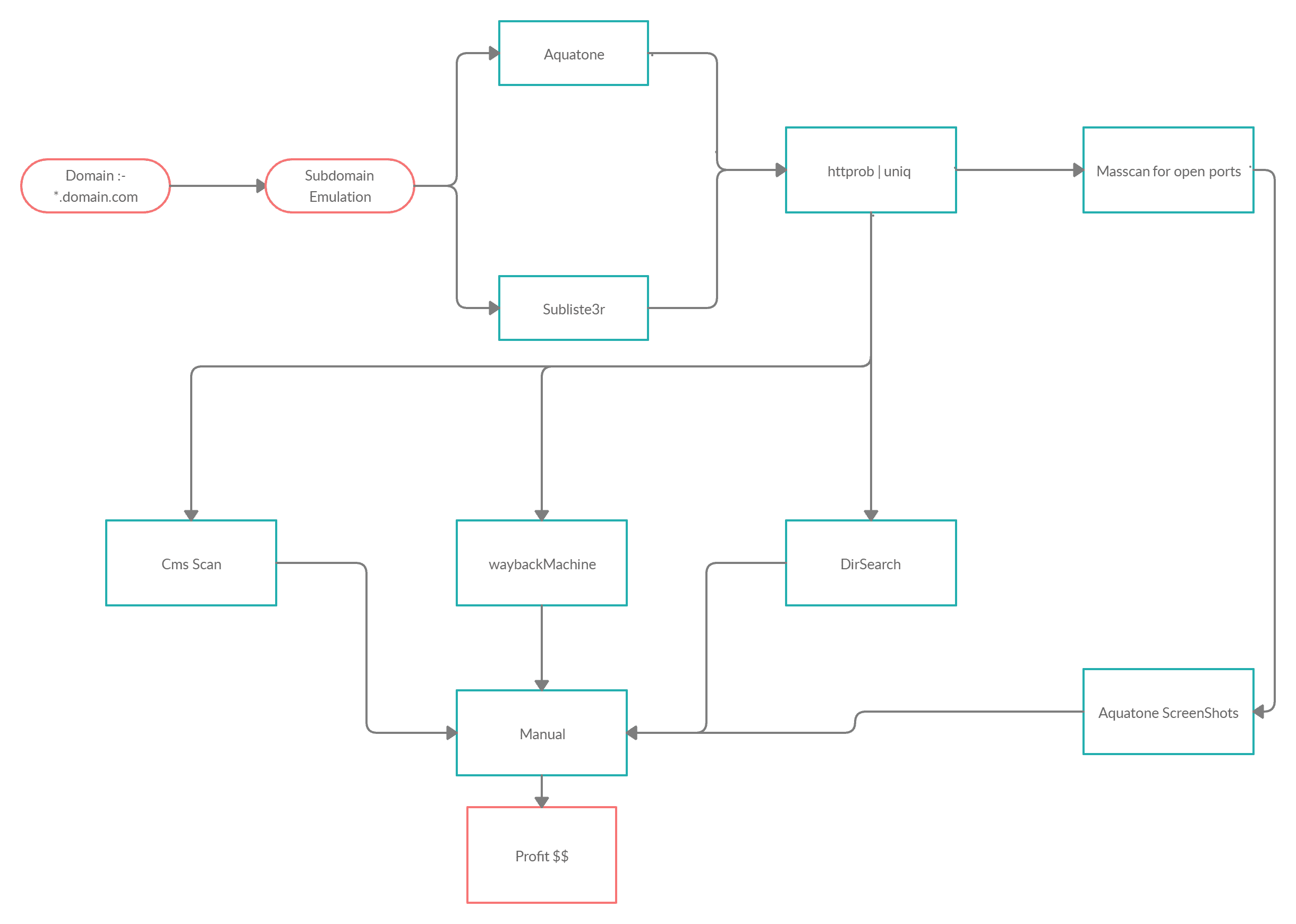
Features
- Subdomain Scan Using Aquatone & Sublist3r
- Httprob for only Live sites
- Masscan for open ports
- Identifing CMS using CMSeeK
- Grabing URL’s from waybackMachine
- ScreenShot using Aquatone
- Brute forcing directories and files using Dirsearch