From hackread.com
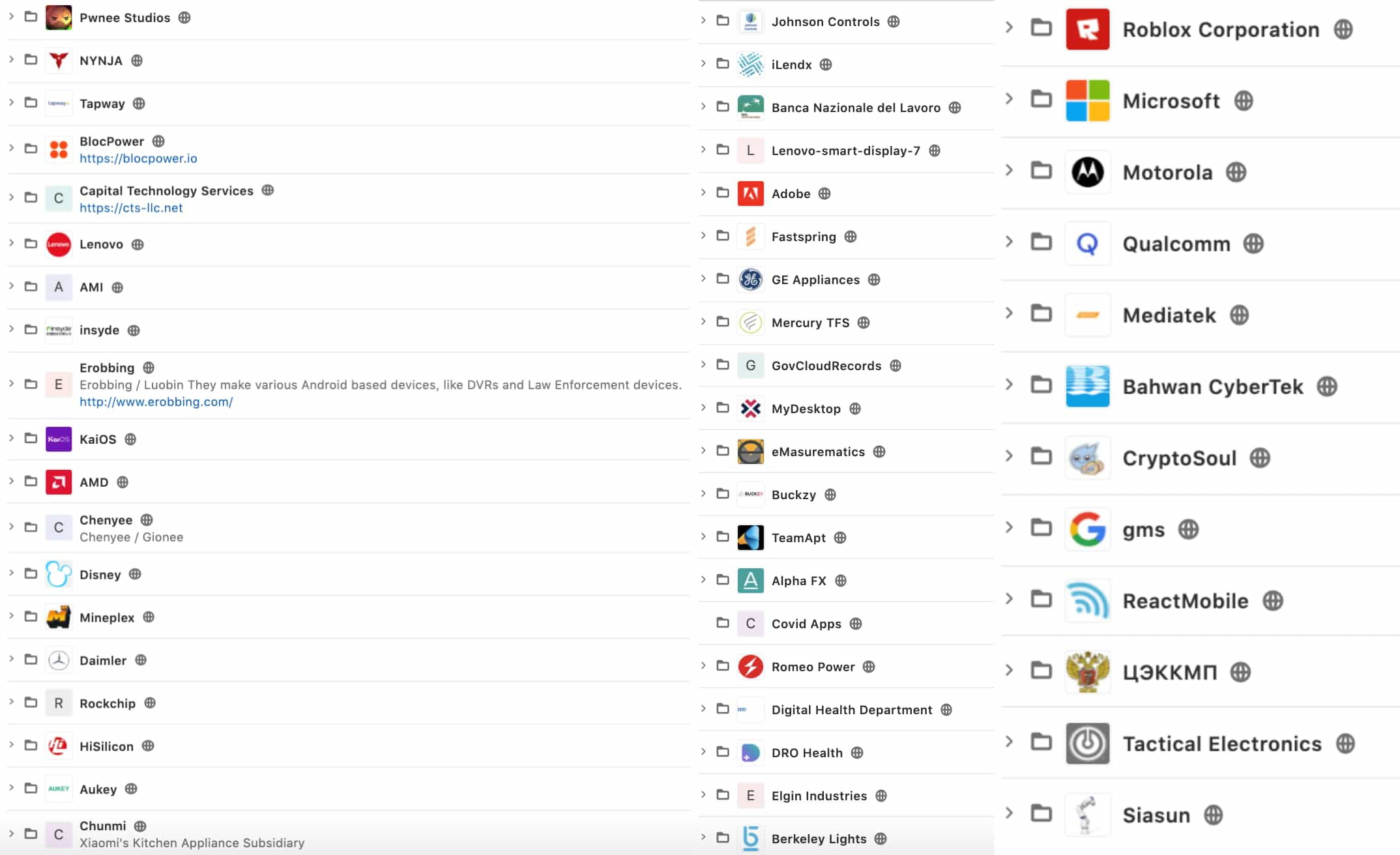
A misconfiguration in the infrastructure of repositories resulted in leaking the source code of dozens of mainstream, high-profile organizations from diverse sectors from tech, food, retail, finance, manufacturing, and e-commerce.
From hackread.com

A misconfiguration in the infrastructure of repositories resulted in leaking the source code of dozens of mainstream, high-profile organizations from diverse sectors from tech, food, retail, finance, manufacturing, and e-commerce.