From trendmicro.com
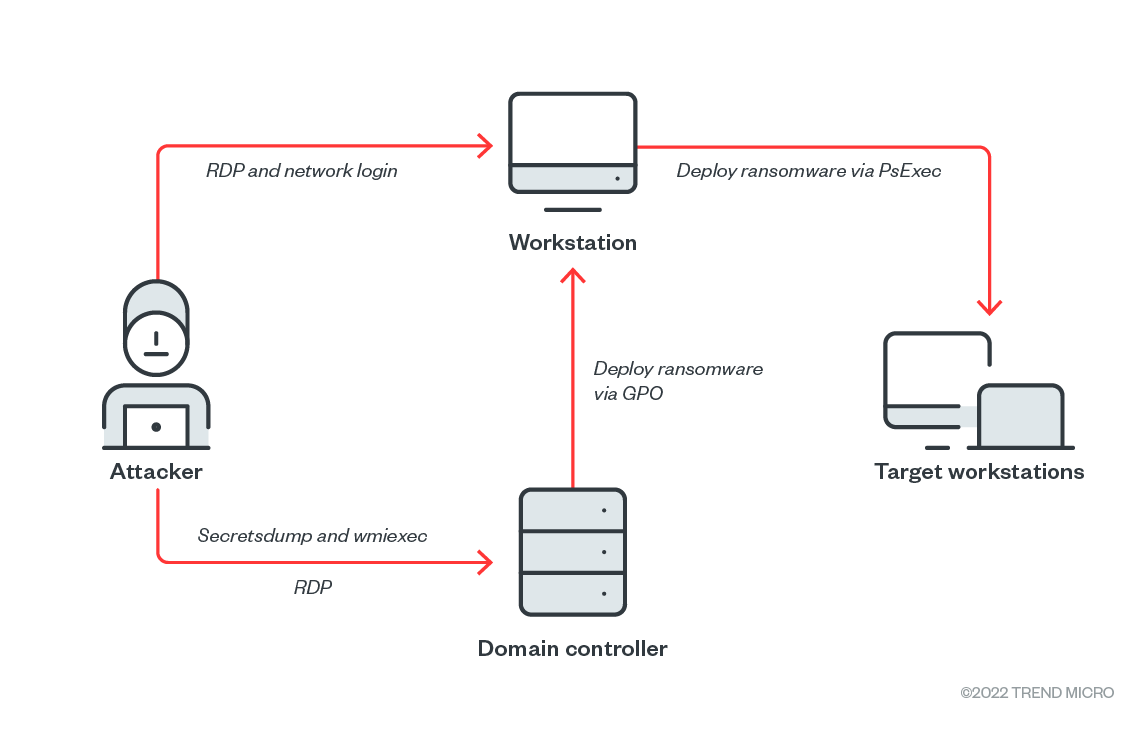
There have already been reports on code-signed rootkits like Netfilter, FiveSys, and Fire Chili. These rootkits are usually signed with stolen certificates or are falsely validated. However, when a legitimate driver is used as a rootkit, that’s a different story. Such is the case of mhyprot2.sys, a vulnerable anti-cheat driver for the popular role-playing game Genshin Impact. The driver is currently being abused by a ransomware actor to kill antivirus processes and services for mass-deploying ransomware. Security teams and defenders should note that mhyprot2.sys can be integrated into any malware.