From kitploit.com
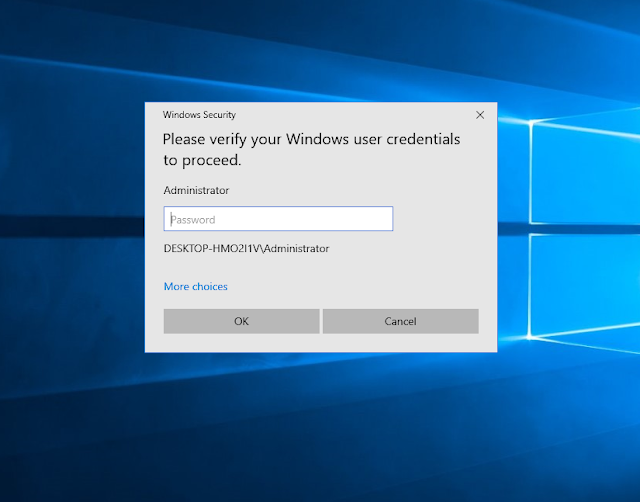
Operational Usage – 1
Nowadays, since the operating system of many end users is Windows 10, we cannot easily steal account information with Mimikatz-like projects like the old days. Using Pickl3, you can try to steal the account information of the active user without escalating the privileges.