From thehackernews.com
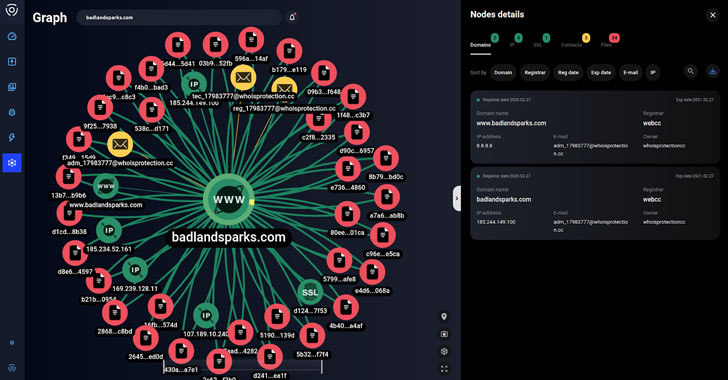
A cybercrime group known for targeting e-commerce websites unleashed a “multi-stage malicious campaign” earlier this year designed with an intent to distribute information stealers and JavaScript-based payment skimmers.
In a new report published today and shared with The Hacker News, Singapore-based cybersecurity firm Group-IB attributed the operation to the same group that’s been linked to a separate attack aimed at online merchants using password-stealing malware to infect their websites with FakeSecurity JavaScript-sniffers (JS-sniffers).