From securityinbits.com
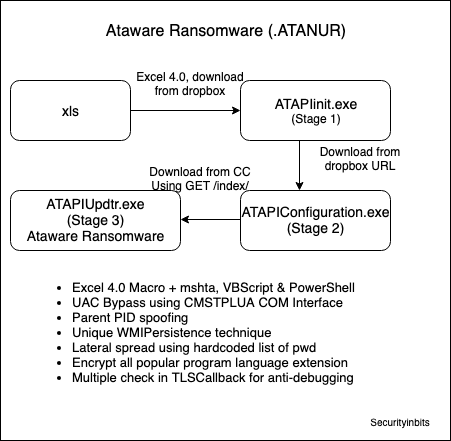
Ataware Ransomware Stage 2 uses Parent PID Spoofing technique to change its parent PID to lsass.exe and this article is also referred to in Mitre Attack website [4]. You may download the ATAPIConfiguration.exe file from ANY.RUN (MD5: 04a2e6400b22a3a5e5e277eceaf2ce0c)Please check previous posts, if you are interested in the complete infection chain Excel 4.0 Macro Analysis – Ataware Ransomware Part 1 & UAC bypass analysis (Stage 1) Ataware Ransomware Part 2.