From securityweek.com
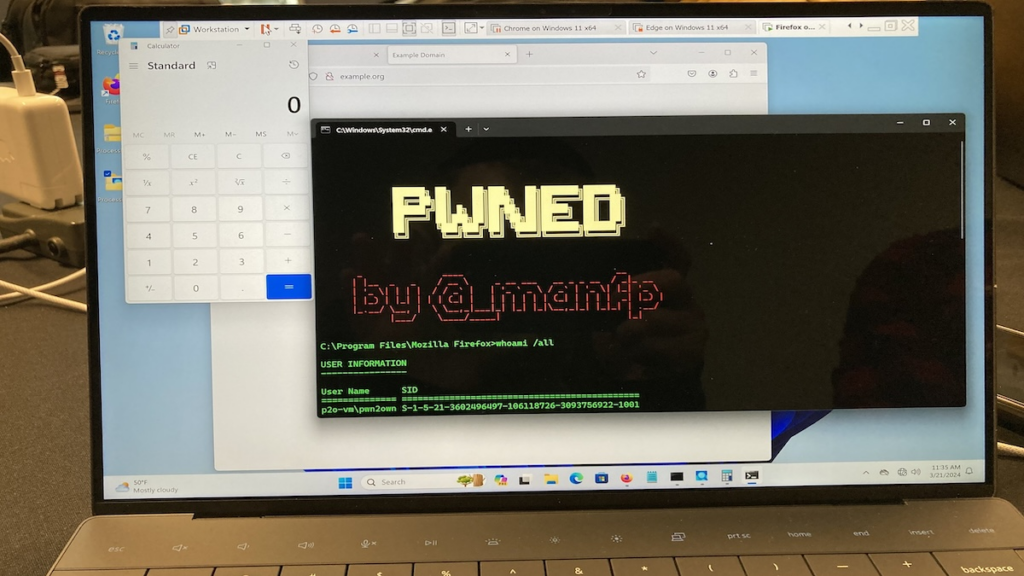
Mozilla has released Firefox browser updates to patch two zero-day vulnerabilities that were exploited at the Pwn2Own Vancouver 2024 hacking contest last week.
The issues, discovered by security researcher Manfred Paul, were chained together to escape the browser’s sandbox and execute code on the system.
Tracked as CVE-2024-29943, the first vulnerability is described as an out-of-bounds access flaw that leads to the bypass of range analysis.
“An attacker was able to perform an out-of-bounds read or write on a JavaScript object by fooling range-based bounds check elimination,” Mozilla explains in its advisory.
The second bug, CVE-2024-29944, is a privileged JavaScript execution issue in event handlers, leading to a sandbox escape.
“An attacker was able to inject an event handler into a privileged object that would allow arbitrary JavaScript execution in the parent process,” Mozilla says.