From 2-spyware.com
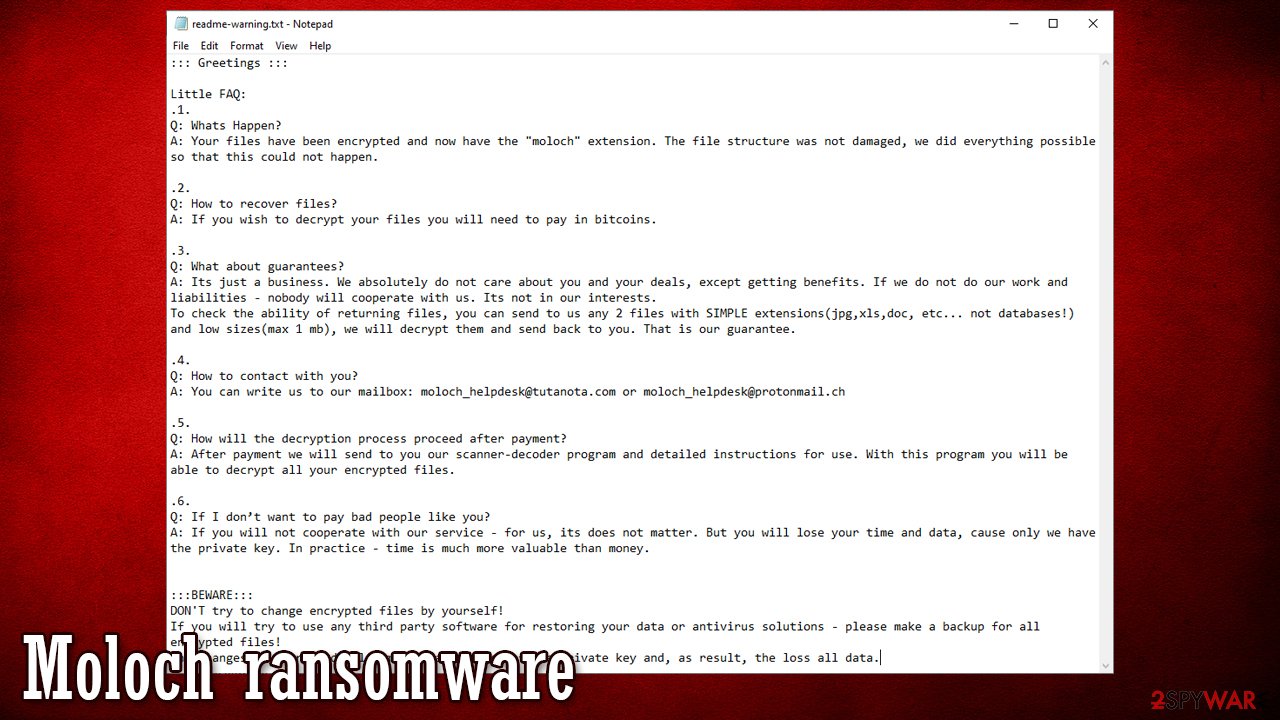
Moloch ransomware is a computer virus infection that encrypts all personal victim files on an affected device and demands a ransom for unlocking them. This file-locking parasite belongs to a relatively small Makop ransomware family compared to others, such as Djvu or Dharma.