From trendmicro.com
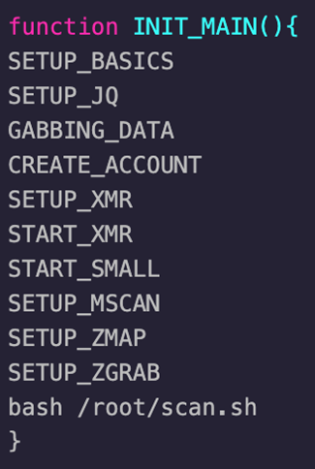
We recently spotted new attacks where, again, threat actors used shell scripts to perform malicious activities. These scripts came from a random image on a public container repository; users should be aware of the security risks of running such, as they may contain malicious elements such as backdoors. Based on previous attacks, these malicious scripts were typically used to deploy cryptocurrency miners. But recent cases involving these fresh samples highlighted how the scripts are developed, as they now serve other purposes besides being downloaders for cryptominers.