From securityonline.info
LightMe
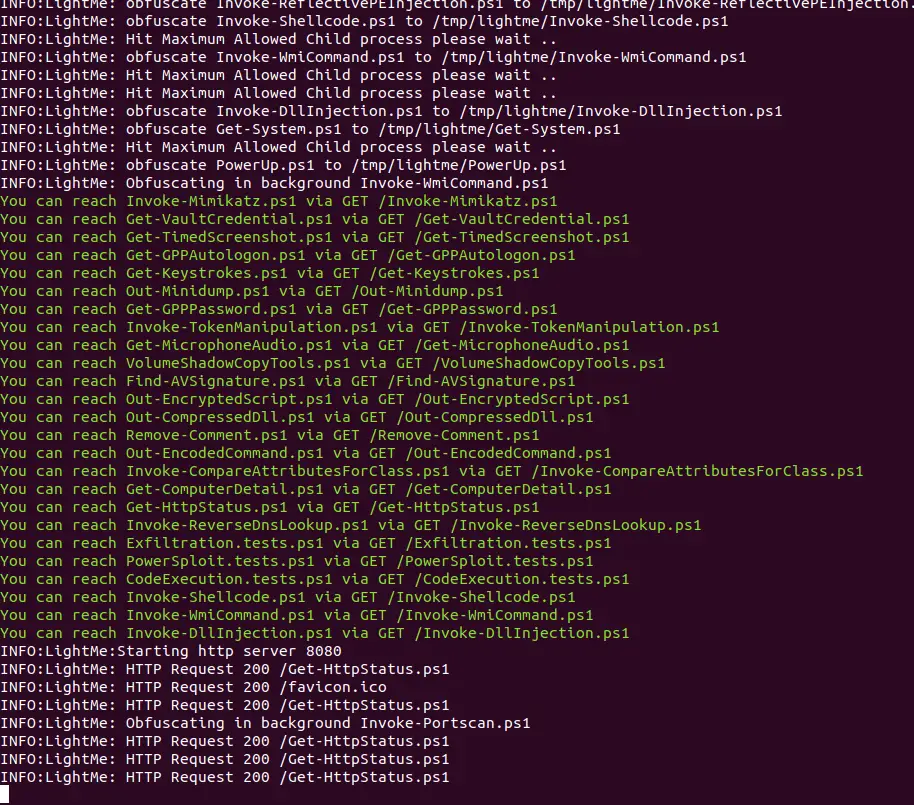
LightMe is a Simple HTTP Server serving Powershell Scripts/Payloads after Obfuscate them and run obfuscation as a service in the background in order to keep obfuscate the payloads which giving an almost new obfuscated payload on each HTTP request.