From malware.news
A few years back, I published my tactical exploitation toolkit, which includes some offensive security tools to assist penetration testers and red teamers during their engagements:
“I’ve always been a big proponent of a tactical approach to penetration testing that does not focus on exploiting known software vulnerabilities, but relies on old school techniques such as information gathering and brute force. While being able to appreciate the occasional usefulness of a well-timed 0day, as a veteran penetration tester I favor an exploit-less approach. Tactical exploitation provides a smoother and more reliable way of compromising targets by leveraging process vulnerabilities, while minimizing attack detection and other undesired side effects.”
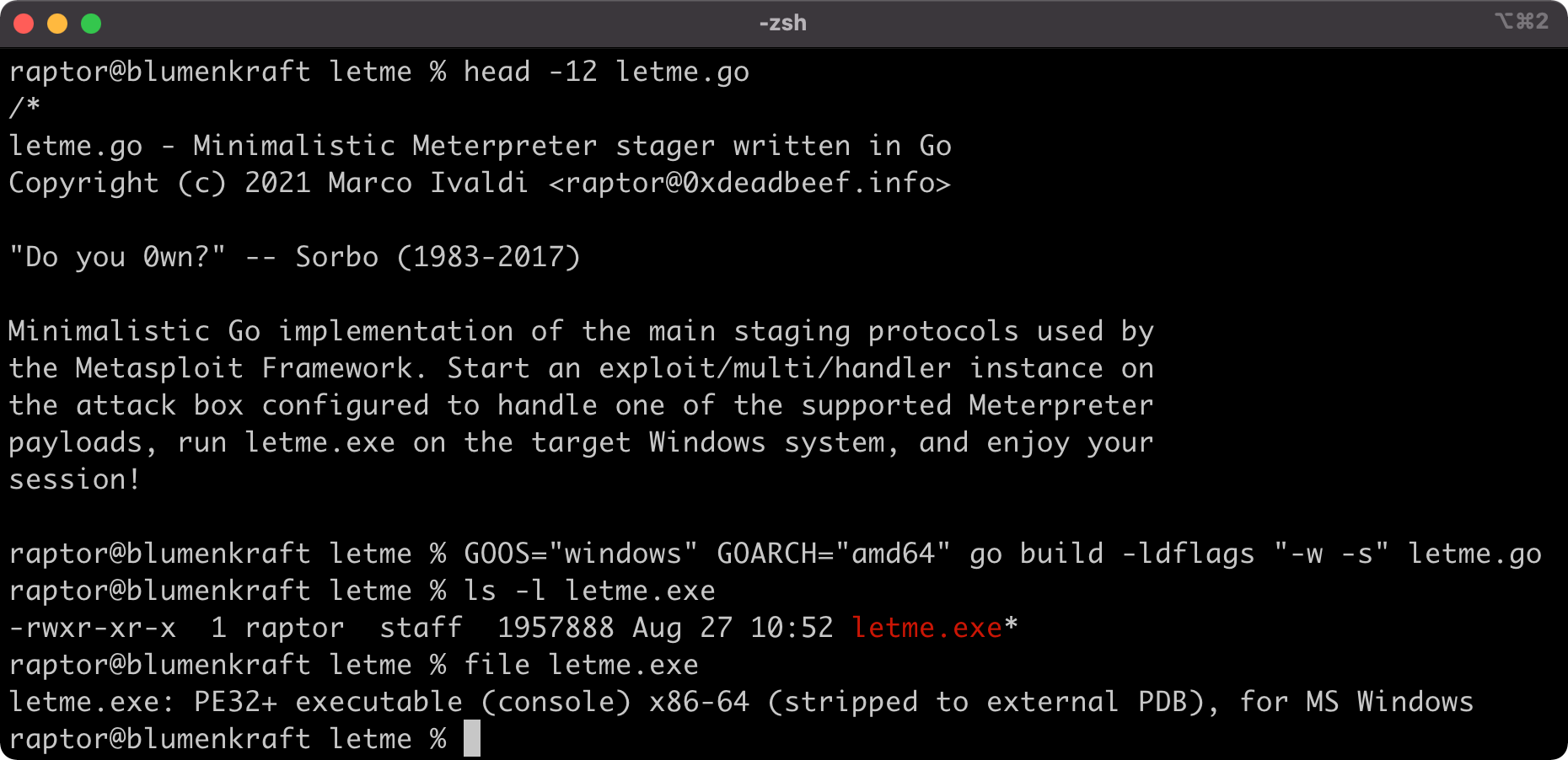
One of my favorite tools that saved me and my team a lot of hassle in countless occasions is letmein.ps1, a PowerShell implementation of the staging protocols used by the Metasploit Framework. If used properly, it’s still able to provide you with a Meterpreter session on Windows without triggering most anti-malware mechanisms, despite being public since 2018. In the same toolkit, I also provided an alternative Python implementation for educational purposes, but its use is not recommended in the field.