From asec.ahnlab.com
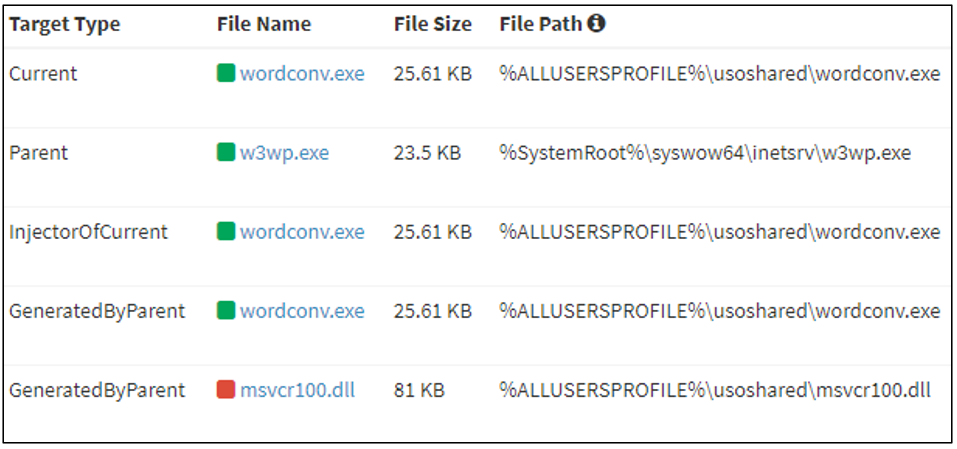
AhnLab Security Emergency response Center (ASEC) has recently confirmed the Lazarus group, a group known to receive support on a national scale, carrying out attacks against Windows IIS web servers. Ordinarily, when threat actors perform a scan and find a web server with a vulnerable version, they use the vulnerability suitable for the version to install a web shell or execute malicious commands. The AhnLab Smart Defense (ASD) log displayed below in Figure 1 shows that Windows server systems are being targeted for attacks, and malicious behaviors are being carried out through w3wp.exe, an IIS web server process. Therefore, it can be assumed that the threat actor uses poorly managed or vulnerable web servers as their initial breach routes before executing their malicious commands later.
The threat actor places a malicious DLL (msvcr100.dll) in the same folder path as a normal application (Wordconv.exe) via the Windows IIS web server process, w3wp.exe. They then execute the normal application to initiate the execution of the malicious DLL. In MITRE ATT&CK, this method of attack is categorized as the DLL side-loading (T1574.002) technique.