From isc.sans.edu
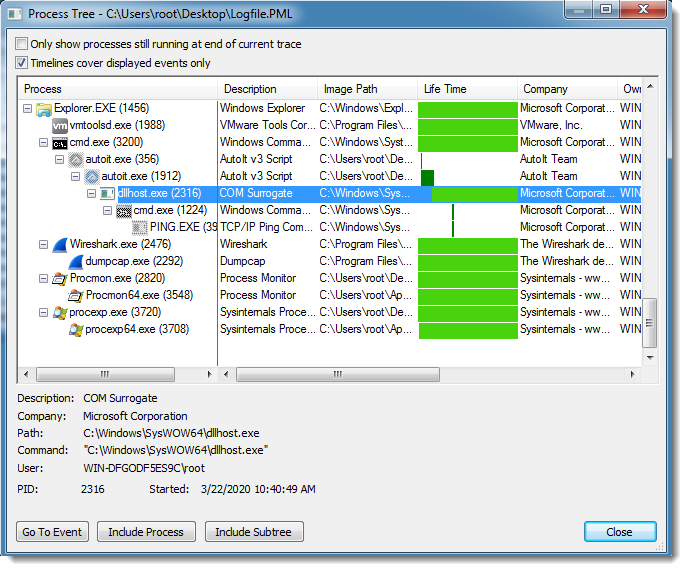
In this diary entry, I’ll share more details on how I obtained the decrypted KPOT EXE. Also take a look at “Reader Analysis: “Dynamic analysis technique to get decrypted KPOT Malware.”, a reader’s analysis.
To obtain the decrypted EXE, I used dynamic analysis. By executing the AutoIt interpreter with the decoded AutoIt script, the shellcode in the AutoIt script decrypted the KPOT EXE and injected it in a dllhost.exe process (process hollowing):