From securityonline.info
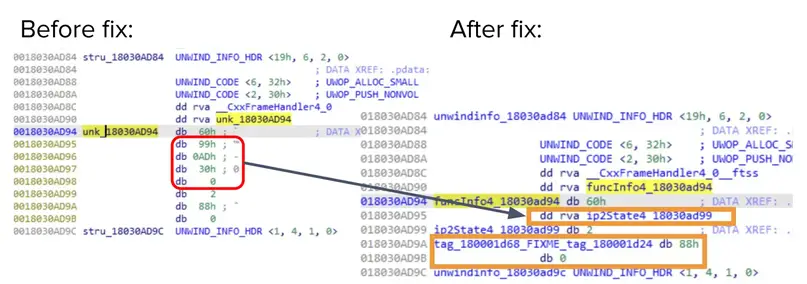
The working flow is simple:
- Dump object files (COFF) directly from one executable binary.
- Link the object files into a new binary, almost the same as the old one.
- During the dumping process, you can insert any data/code at any location.
- SBI is just one of the using scenarios, especially useful for black-box fuzzing.