Information
This decryptor will not work if you have shutdown or restart the infected computer since your files were encrypted.
You must run this decryptor on the infected computer, against the original encrypted files otherwise the key calculation may fail.
Usage
1. Run the decryptor by double-clicking it or via Powershell/cmd.
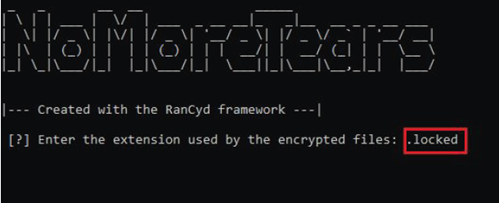
2. When the decryptor starts, enter the extension that has been added to your encrypted files by the ransomware (e.g. locked, hidden tear).
3. Choose the validation method you wish to use. The validation process will use a single file to calculate the decryption key, once it has identified the key the rest of your files will be decrypted.
a. Content match (1) will search the specified file for a specific piece of content that you provide. For example, if you know that the file originally contained the phrase “the quick brown fox”, the decryptor will use that phrase to confirm it has found the correct key.
b. Exact file match (2) is useful if you have an exact, unencrypted copy of one of the encrypted files. If you have such a copy, the decryptor will use the entire file to confirm it has found the correct key.
4. Provide your validation data.
Developed by Alex Seymour
Download the decryptor here