From github.com
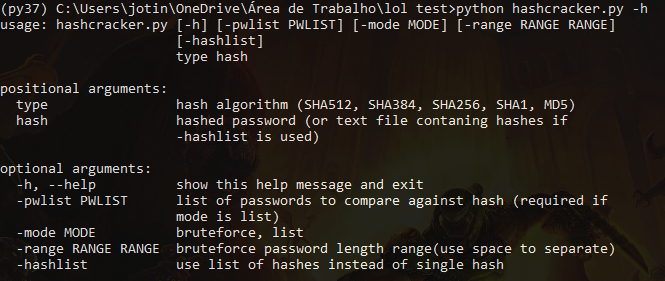
HashCracker is a python hash cracker which support hashing algorithms like SHA512, SHA256, SHA384, SHA1, MD5, SHA224.
- Auto detection of hashing algorithm based on length (not recommended)
- Bruteforce
- Password List
From github.com

HashCracker is a python hash cracker which support hashing algorithms like SHA512, SHA256, SHA384, SHA1, MD5, SHA224.