From thehackernews.com
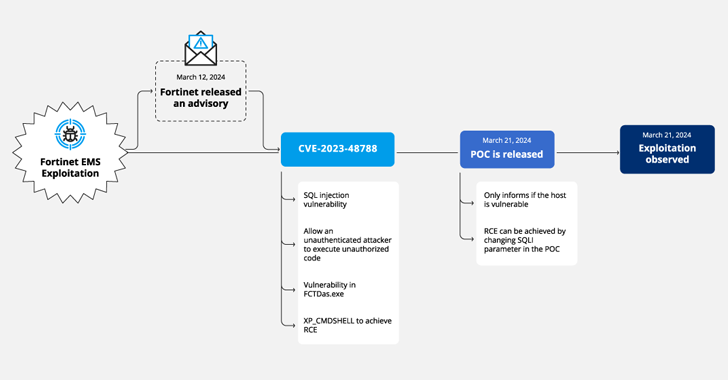
Cybersecurity researchers have discovered a new campaign that’s exploiting a recently disclosed security flaw in Fortinet FortiClient EMS devices to deliver ScreenConnect and Metasploit Powerfun payloads.
The activity entails the exploitation of CVE-2023-48788 (CVSS score: 9.3), a critical SQL injection flaw that could permit an unauthenticated attacker to execute unauthorized code or commands via specifically crafted requests.
Cybersecurity firm Forescout is tracking the campaign under the codename Connect:fun owing to the use of ScreenConnect and Powerfun for post-exploitation.