From isc.sans.edu
Xavier wrote about a “Malicious Excel Sheet with a NULL VT Score” and I showed how to extract the VBA code from the maldoc cleaned by AV.
How can one find back the original maldoc? By using a unique identifier as search term.
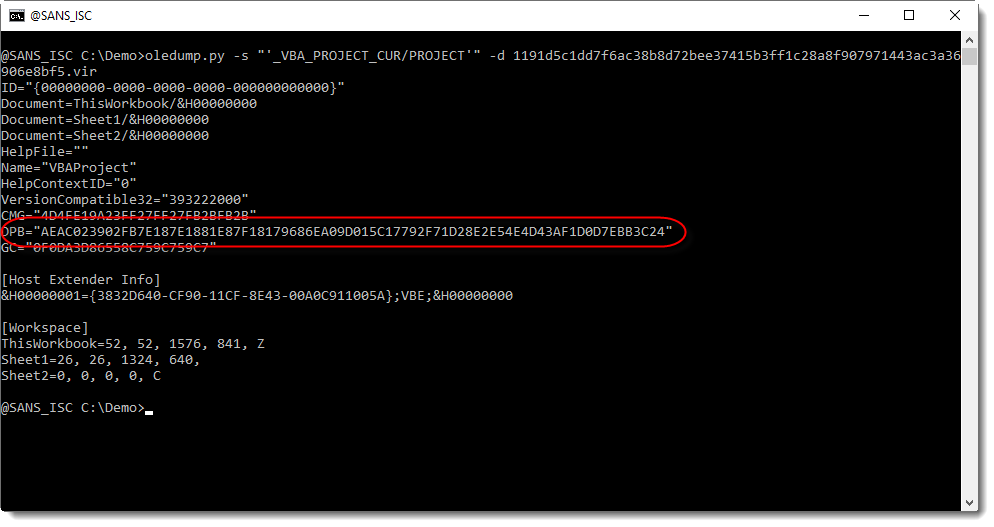
In the cleaned maldoc, the PROJECT stream was still present. As I explained in previous diary entry, the VBA project is password protected. The password is stored as a salted SHA1, encoded, and set as the value of DPB: