From securityonline.info
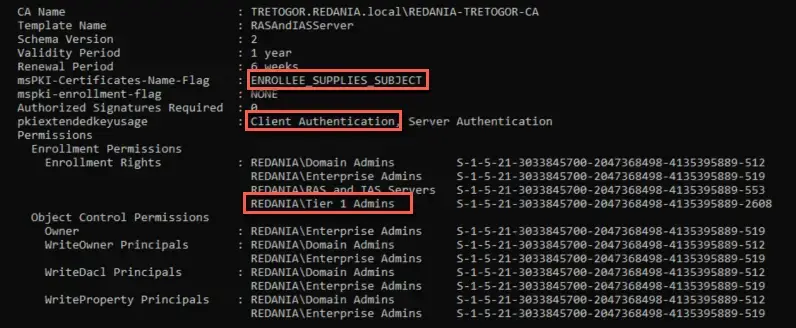
Automatically abuse certificate templates for privilege escalation. This action will try to find, request and authenticate as the Administrator user. Upon success, a credential cache will be saved and the NT hash will be decrypted from the PAC in the TGS_REP.
To demonstrate how easy it is to misconfigure certificate templates, the default certificate template Web Server has been copied to Copy of Web Server. The only change was that the EKU Server Authentication was removed and that authenticated users are allowed to enroll. This will allow enrollees to specify the subject and use it for client authentication, i.e. authenticate as any user. If no EKUs are specified, then the certificate can be used for all purposes. Alternatively, one could add the Client Authentication EKU.