From blogs.jpcert.or.jp
Around February 2023, JPCERT/CC identified an attack that attempted to infect a crypto asset exchanger with the Parallax RAT malware. This attack attempted to infect employees of the crypto asset exchanger with malware by sending spam emails. This article presents the details of this attack.
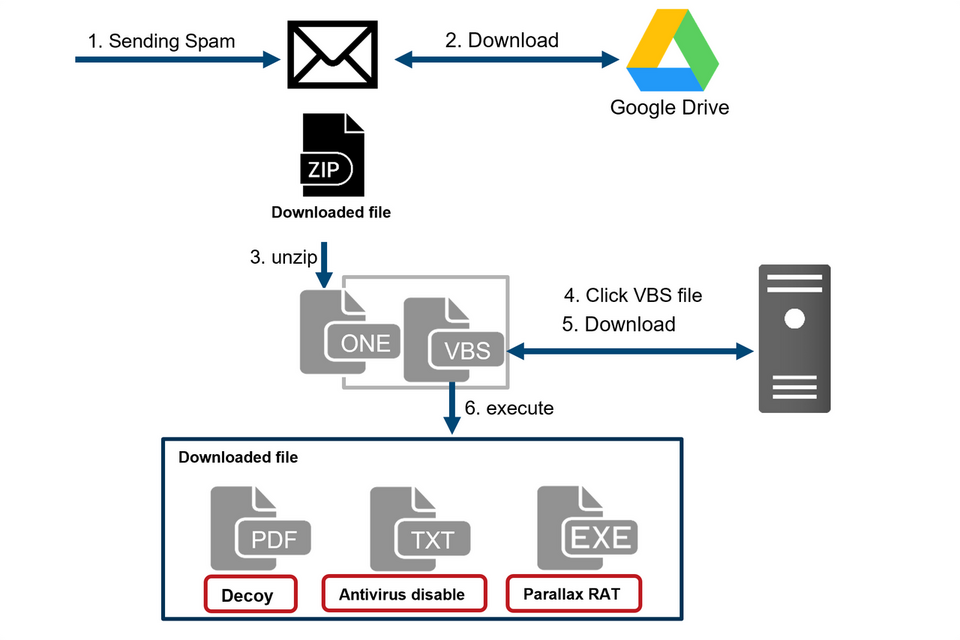
Flow of events leading to Parallax RAT infection
Figure 1 shows the flow of this attack. The identified attack starts with a spam email, which urges the user to download a file from a Google Drive link on it. Once the user accesses Google Drive, a ZIP file containing a OneNote file is downloaded. When it is opened, a document appears prompting the user to click the VBS files embedded inside. If the target runs one of the VBS files, it downloads and runs several files including Parallax RAT.