From any.run
1. Steganography
We identified a new phishing campaign utilizing steganography, a technique historically seldom used due to its complexity. However, its application has notably increased.
Read our analysis of steganography in phishing.
As of recently, the campaign subsided, but new samples suggest its resurgence — as seen in this sample.
This new campaign employs steganography in multiple stages:
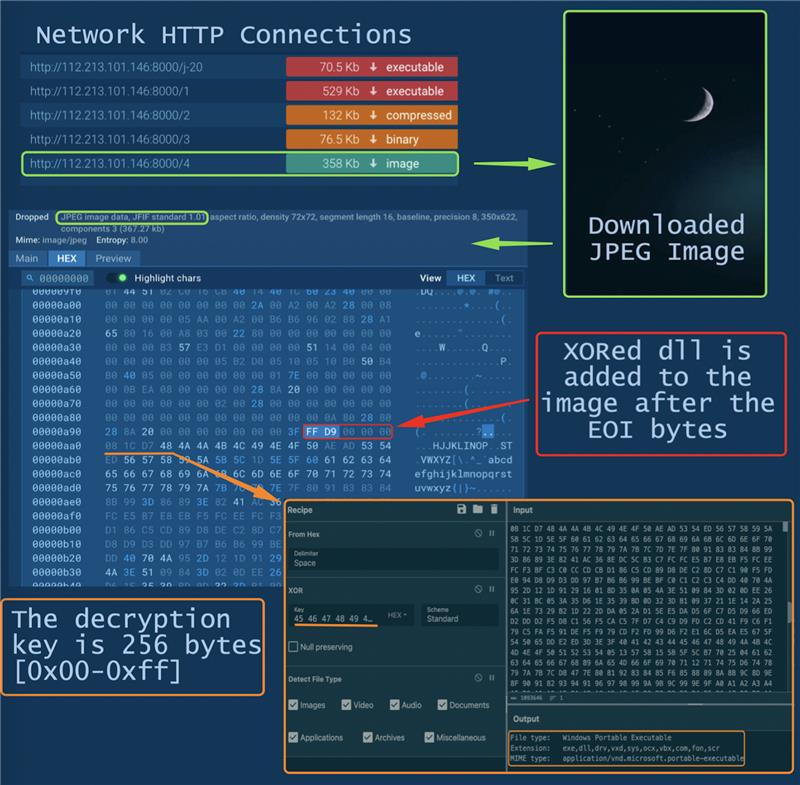
- The modified “Google Update” app downloads multiple PE files and an image containing a DLL
- TrueUpdate, downloaded in the previous step, extracts and decrypts the DLL from the image file with 256 bytes XOR key and transfers control to the received DLL
- Then a malicious module comes into play, hosting a Remote Access Trojan and intercepting control. The actions of gh0strat become evident on the network at the specified address: 112.213.101.146:7700
You can find more samples that employ steganography in ANY.RUN’s public submissions — just search by tag #stego or use this link.