Information
This decryptor has only been tested again the sequre variant of CryptConsole. Files encrypted by this variant will have sequre@tuta.io at the start of their name. Due to the ransomware’s unreliable encryption routine, some files may be unrecoverable. This decryptor is capable of recovering the original name for encrypted files. Files that are decrypted will also have their original name restored.
If you are unable to access the file browser because the ransomware has encrypted your quick launch items and start menu items you can access it by holding down the windows key (between CTRL and ALT) and pressing R, then enter explorer in the windows that appear and press enter.
Usage
1. Run the decryptor with administrator privileges by right-clicking on it and selecting ‘Run as administrator’. Without administrator permissions, the decryptor will not be able to decrypt files in protected locations.
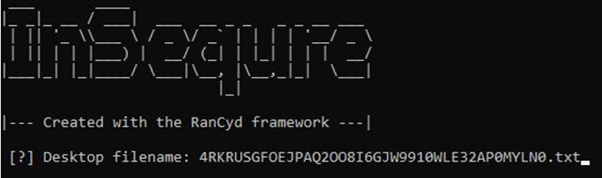
2. The ransomware will have left a text file on your desktop, enter the name (and extension) of the file so the decryptor can extract the required information from it.
3. Decide if you would like the decryptor to delete encrypted files after it successfully decrypts them. If the decryptor fails to decrypt a file it will not be removed.
4. Wait until the decryptor completes. If the decryptor is unable to decrypt any files it will list them in a file on your desktop. The decryptor will also attempt to remove all of the ransom notes from your system.
Developed by Alex Seymour
Download the decryptor here