From youtube.com
Category: News
The Network is Key to Securing the Everywhere Perimeter
From securityboulevard.com

In light of surging ransomware cases and recent high-profile cyberattacks like those on SolarWinds, Colonial Pipeline, and meat supplier JBS, enterprise security teams may fall into the trap of thinking, “more defenses are better.” They implement an arsenal of point solutions, hoping their bases will be covered. The reality is, an organization can spend as much as they can afford and add as many tools as they want to their portfolio–but if the underlying network infrastructure is not secure, these tools may not make a difference.
The way businesses often approach network security hasn’t kept pace with the demands of the increasingly distributed workforce or attacker sophistication. In the past, the hard edges of the traditional firewall were enough to protect an organization against outside access. But with today’s highly distributed workforce and the proliferation of IoT and personal devices, the traditional perimeter is obsolete. It’s nearly impossible to identify a rigid perimeter, with connections spanning the campus edge, user devices, IoT devices and both public and private clouds.
Zero-day Exploit Detected in Adobe Experience Manager
From ehackingnews.com

A zero-day vulnerability in a prominent content management solution used by high-profile firms such as Deloitte, Dell, and Microsoft has been found.
The flaw in Adobe Experience Manager (AEM) was detected by two members of Detectify’s ethical hacking community.
Adobe Experience Manager (AEM) is a popular content management system for developing digital customer experiences like websites, mobile apps, and forms. AEM has become the primary Content Management System (CMS) for many high-profile businesses due to its comprehensiveness and ease of use.
Threat modeling needs a reset
From helpnetsecurity.com

The traditional approaches to threat modeling can be very effective, but they don’t scale well enough in the current computing and threat landscape. As more business operations shift to digital it becomes too time consuming to tackle all of an organization’s high-priority threats, leaving too many vulnerabilities unaddressed.
How can this process be streamlined? Organizations should start by realizing that they are doing threat modeling backwards, and that they need to reverse how these models are developed.
SolarWinds hackers remained hidden in Denmark’s central bank for months
From securityaffairs.co

Russia-linked threat actors infected the systems of Denmark’s central bank (Danmarks Nationalbank) and maintained access to its network for more than six months.
The security breach is the result of the SolarWinds supply chain attack that was carried out by the Nobelium APT group (aka APT29, Cozy Bear, and The Dukes).
The intrusion was revealed by the technology outlet Version2, which obtained official documents from the Danish central bank through a freedom of information request.
“Some of the world’s most sophisticated hackers have had an IT backdoor at Danmarks Nationalbank for seven months. Danmarks Nationalbank itself cannot rule out that the suspected Russian state hackers have abused the back door to further compromise Danmarks Nationalbank.” states Version2.
BIOS Disconnect: New High-Severity Bugs Affect 128 Dell PC and Tablet Models
From thehackernews.com
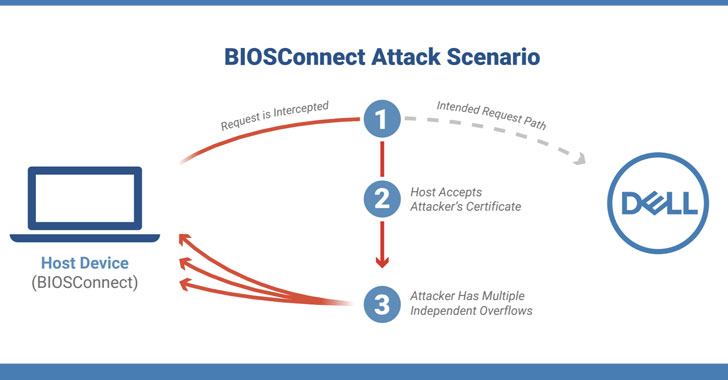
Cybersecurity researchers on Thursday disclosed a chain of vulnerabilities affecting the BIOSConnect feature within Dell Client BIOS that could be abused by a privileged network adversary to gain arbitrary code execution at the BIOS/UEFI level of the affected device.
“As the attacker has the ability to remotely execute code in the pre-boot environment, this can be used to subvert the operating system and undermine fundamental trust in the device,” researchers from enterprise device security firm Eclypsium said. “The virtually unlimited control over a device that this attack can provide makes the fruit of the labor well worth it for the attacker.”
GitHub Launches ‘Copilot’ — AI-Powered Code Completion Tool
From thehackernews.com
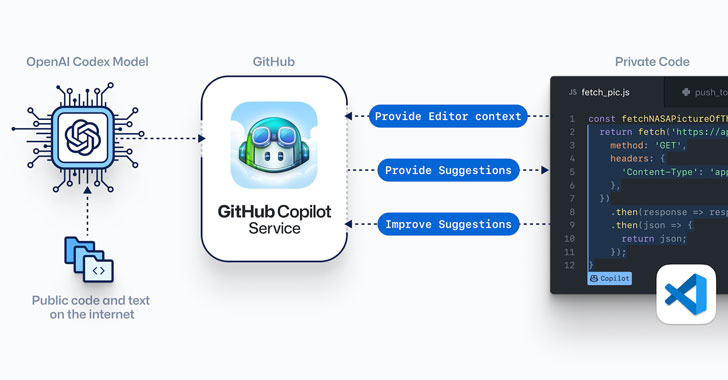
GitHub on Tuesday launched a technical preview of a new AI-powered pair programming tool that aims to help software developers write better code across a variety of programming languages, including Python, JavaScript, TypeScript, Ruby, and Go.
Copilot, as the code synthesizer is called, has been developed in collaboration with OpenAI, and leverages Codex, a new AI system that’s trained on publicly available source code and natural language with the goal of translating comments and code written by a user into auto-generated code snippets.