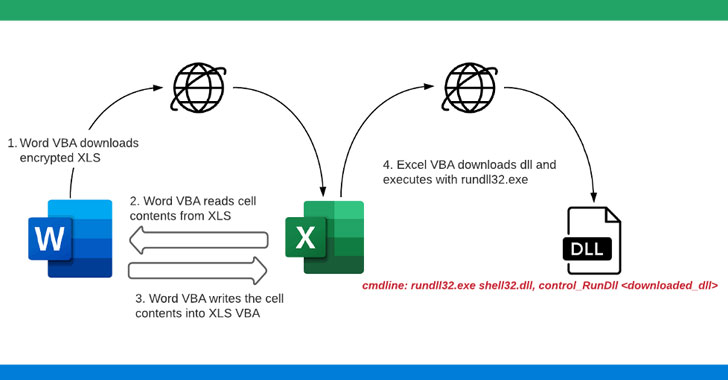
From gbhackers.com

A brand-new technique has been used by the hackers of the Magecart threat group recently to hide stolen credit card data in the images.
In general, the threat actors of Magecart target the e-commerce websites, as their main motive is to steal credit card details. Once they are done with the stealing process, the threat actors sell the stolen data in the underground markets in Darkweb.
However, the experts opined that the threat actors usually obfuscate the malware code inside comment sections and encode the data into images that are hosted in the server.