From latesthackingnews.com

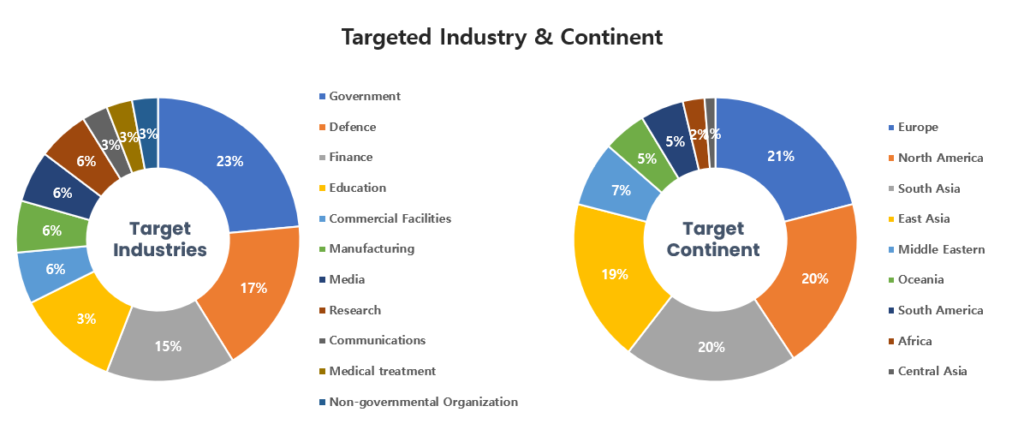
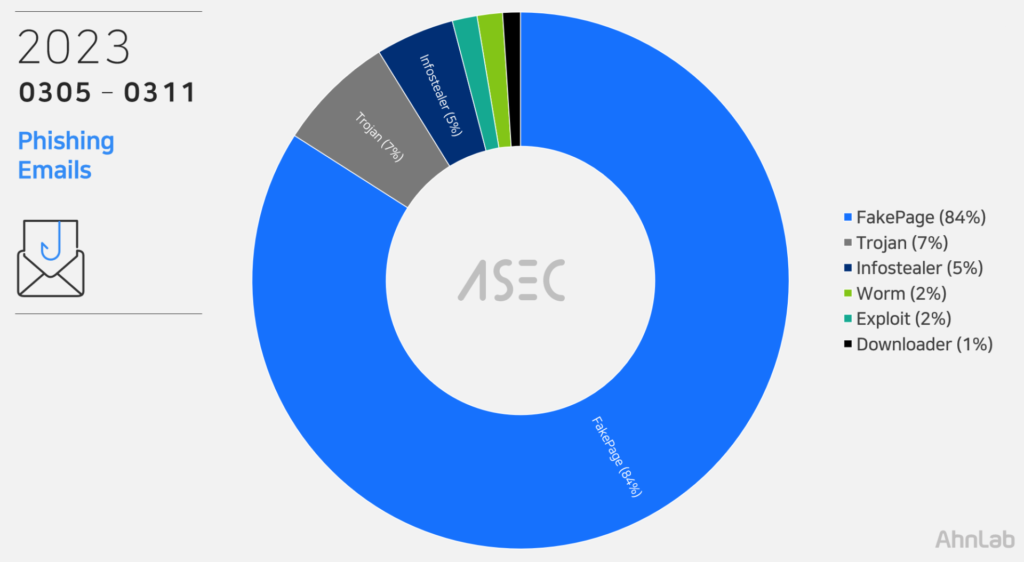
As cyber threats continue to grow, Europe, with its highly digitalized economy, has become a prime target. In fact, the number of cyberattacks on European businesses has soared to unprecedented heights, with a 108% increase in attacks against key sectors since 2020. To combat this alarming trend, the European Parliament has introduced NIS2, a new cybersecurity directive aimed at enhancing the Union’s cyber resilience. NIS2 brings tighter requirements and a renewed emphasis on risk management and incident response, forever changing the way EU businesses tackle cybersecurity. In this blog post, we’ll delve into the far-reaching consequences of NIS2 for European cybersecurity and provide essential insights to help businesses adapt and thrive in this new regulatory landscape.