From intel471.com
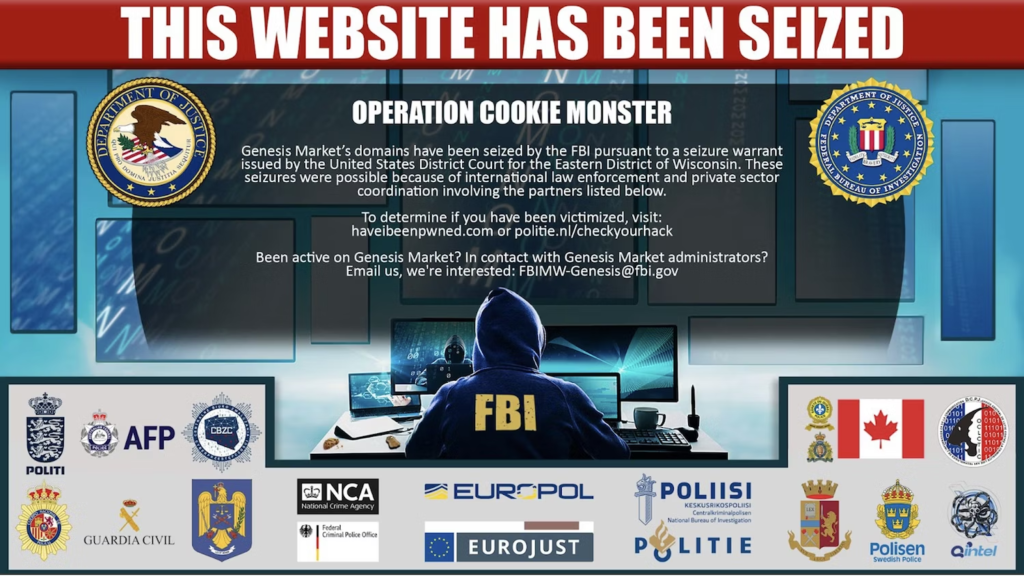
Cybercrime has become increasingly challenging to defend against because of its scale, which has been enabled by the cybercrime-as-a-service economy. Rather than lone wolf cybercriminals performing every task needed to compromise and monetize a computer or account, those tasks are now covered by specialists. Malware and botnets can be rented. Vulnerability information can be purchased. Cybercriminals no longer have to learn how to do every action to execute an operation. They can buy the components or services needed for a specific fraud, allowing them to focus their energy on the part that delivers illicit revenue. A key component of cybercrime-as-a-service is the sale of login credentials or access to accounts.