From blog.qualys.com
The previous blog from this three-part series showcased an overview of the vulnerability threat landscape. To summarize quickly, it illustrated the popular methods of exploiting vulnerabilities and the tactical techniques employed by threat actors, malware, and ransomware groups. Perhaps more crucially, we stated that commonly used solutions (CISA KEV/EPSS) often fall short in identifying high-risk vulnerabilities.
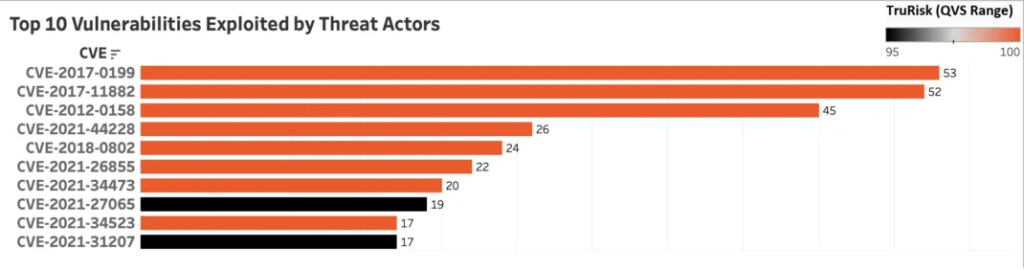
In this blog, we will focus on an insider’s perspective on the threat landscape, viewing it through the eyes of an attacker. We will examine how quickly vulnerabilities get exploited in the wild, identify popularly sought-after vulnerabilities by threat actors, malware, and ransomware groups, and explore their underlying motives.
We will also provide insights on what measures to take you can take to safeguard your organizations from these vulnerabilities.
So, let’s dive headfirst into this intriguing world without further ado.