From securityonline.info
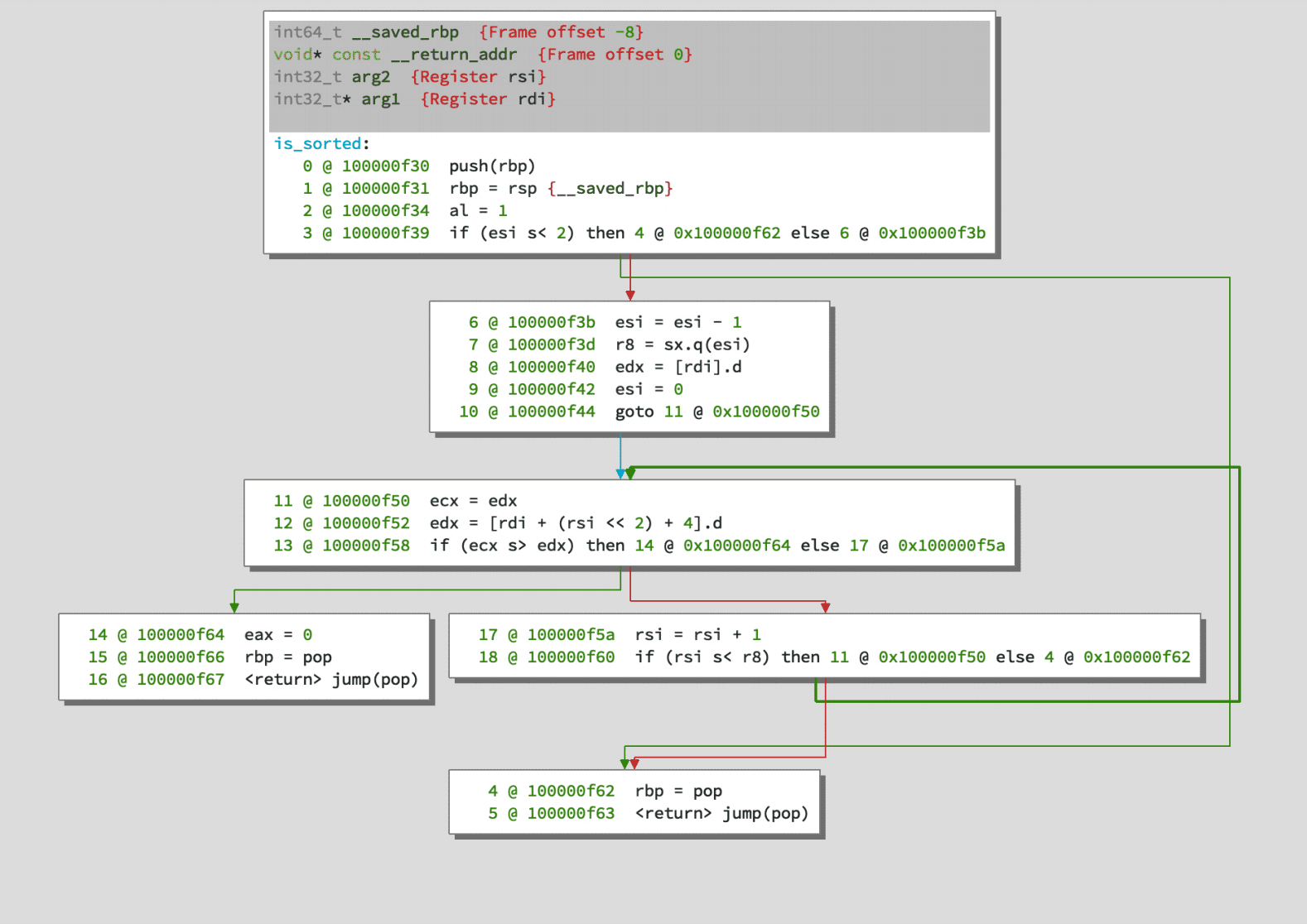
Common approaches to analyzing software for security vulnerabilities are such as source code reviews, static analysis, and fuzzing. Since this thesis focuses on already compiled software source code reviews can not be performed, instead, reverse engineering is needed which can result in a very tedious and time-consuming task.