From 2-spyware.com
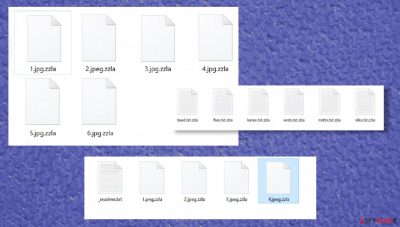
When Zzla ransomware payload file is executed on a Windows computer, it immediately uses military-grade coding algorithms to encrypt all personal files stored on the device. Only system files are left unlocked (but heavily modified) so the infected machine could still boot up.
Then the file-locking parasite generates a ransom note, titled _readme.txt, and leaves it on the desktop and in some affected folders. It’s easy to deduct whether this particular strain of Djvu ransomware family infected your device, as all encrypted files are appended with the .zzla extension.