From securityaffairs.com
esearchers from cybersecurity firm GreyNoise have spotted exploitation attempts for the critical vulnerability CVE-2024-0769 (CVSS score 9.8) impacting all D-Link DIR-859 WiFi routers.
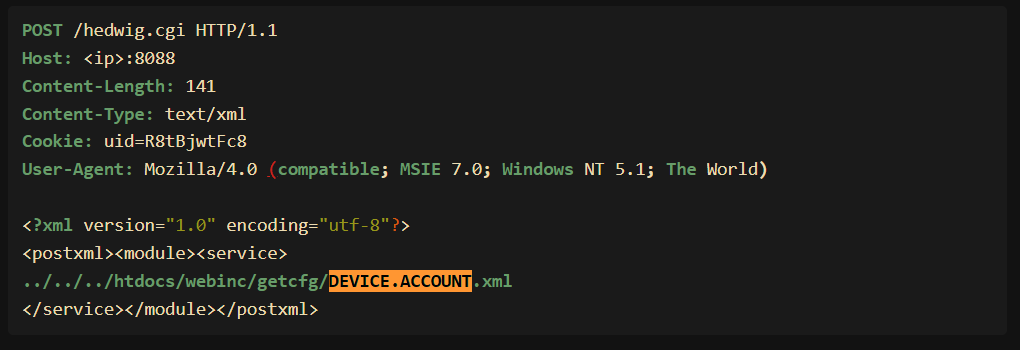
The vulnerability is a path traversal issue that can lead to information disclosure. Threat actors are exploiting the flaw to collect account information, including user passwords, from the vulnerable D-Link DIR-859 WiFi routers.
The vendor states that the DIR-859 family of routers has reached their End of Life (“EOL”)/End of Service Life (“EOS”) life-cycle, and for this reason, the flaw will likely not be addressed.
GreyNoise observed hackers targeting the ‘DEVICE.ACCOUNT.xml’ file to extract all account names, passwords, user groups, and user descriptions on the device. The attackers use a modified version of the public exploit.
“GreyNoise observed a slight variation in-the-wild which leverages the vulnerability to render a different PHP file to dump account names, passwords, groups, and descriptions for all users of the device. At the time of writing we are not aware of the motivations to disclose/collect this information and are actively monitoring it” reads the analysis published by GreyNoise.