From welivesecurity.com
ESET analysts dissect a novel phishing method tailored to Android and iOS users.
[They] discovered a series of phishing campaigns targeting mobile users that used three different URL delivery mechanisms. These mechanisms include automated voice calls, SMS messages, and social media malvertising.
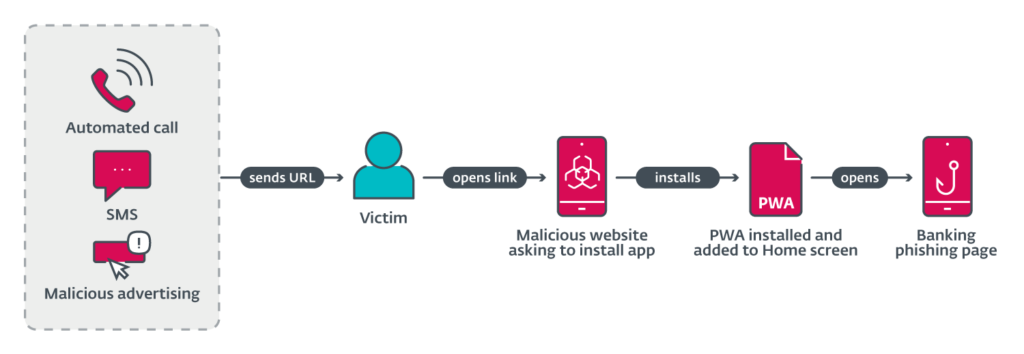
The voice call delivery is done via an automated call that warns the user about an out-of-date banking app and asks the user to select an option on the numerical keyboard. After pressing the correct button, a phishing URL is sent via SMS. This was reported in a tweet, by Michal Bláha.
Initial delivery by SMS was performed by sending messages indiscriminately to Czech phone numbers. The message sent included a phishing link and text to socially engineer victims into visiting the link.

