From thehackernews.com
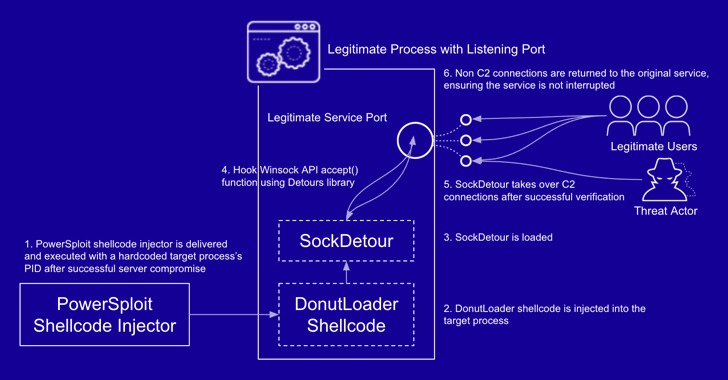
Cybersecurity researchers have taken the wraps off a previously undocumented and stealthy custom malware called SockDetour that targeted U.S.-based defense contractors with the goal of being used as a secondary implant on compromised Windows hosts.
“SockDetour is a backdoor that is designed to remain stealthily on compromised Windows servers so that it can serve as a backup backdoor in case the primary one fails,” Palo Alto Networks’ Unit 42 threat intelligence said in a report published Thursday. “It is difficult to detect, since it operates filelessly and socketlessly on compromised Windows servers.”